Splunk Security Session - .conf Go Köln
- 1. © 2022 SPLUNK INC. Security Session 15. November, Köln
- 2. © 2022 SPLUNK INC.
- 3. © 2019 SPLUNK INC. Matthias Maier Product Marketing Director for Security in EMEA Experience • Since 02.2013 @Splunk • Former LogLogic/TIBCO, McAfee/Intel Security • CEH, CISSP, CISM
- 4. © 2022 SPLUNK INC. Agenda Cyber Security Trends Trends in Security Operations The Splunk Approach Security Product & Solution Update My Top 3 Security Breakouts Next Steps!
- 5. © 2022 SPLUNK INC.
- 6. © 2022 SPLUNK INC. Double Triple Extortion Ransomware (Dreifach Bestrafung) 1989; Mid 2000 until Today Finland Mental Health Triple Extortion Allianz Global Corporate & Speciality
- 7. © 2022 SPLUNK INC. Verletzung der Geheimhaltungs- u. Vertraulichkeits- vereinbarung von Verträgen Vorfall 1
- 8. © 2022 SPLUNK INC. Akquise von Zugangsdaten von Mitarbeitern / Dienstleistern / Zeitarbeitern Vorfall 2
- 9. © 2022 SPLUNK INC. Zerstörung einer Produktionsstätte Vorfall 3
- 10. © 2022 SPLUNK INC. Gesetzliche Vorgaben und Empfehlungen Staatliche Instrumente BSI Mindeststandards IT Sicherheitsgesetz 2.0 KRITIS Sektoren basierte Standards
- 11. © 2022 SPLUNK INC. BSI Mindeststandards Beispiel: Mindeststandard des BSI zur Protokollierung und Detektion von Cyber- Angriffen https://www.bsi.bund.de/DE/Themen/Oeffentliche-Verwaltung/Mindeststandards/PDCA/PDCA_node.html
- 12. © 2022 SPLUNK INC. BSI Mindeststandards Beispiel: Mindeststandard des BSI zur Protokollierung und Detektion von Cyber- Angriffen https://www.bsi.bund.de/DE/Themen/Oeffentliche-Verwaltung/Mindeststandards/PDCA/PDCA_node.html
- 13. © 2022 SPLUNK INC. §8a (1a) Angriffserkennung § 8a (3) Nachweise § 8b Meldepflicht § 8a Absatz 1 BSIG - Konkretisierung der KRITIS-Anforderungen
- 14. © 2022 SPLUNK INC. Trends in Security Operations
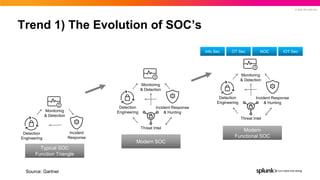
- 15. © 2022 SPLUNK INC. Typical SOC Function Triangle Modern SOC Modern Functional SOC Trend 1) The Evolution of SOC’s Monitoring & Detection Detection Engineering Incident Response Monitoring & Detection Detection Engineering Incident Response & Hunting Threat Intel Monitoring & Detection Detection Engineering Incident Response & Hunting Threat Intel Info Sec OT Sec NOC IOT Sec Source: Gartner
- 16. © 2022 SPLUNK INC. Challenges today… Lack of Visibility Expanding Attack Surface Tooling Complexity Skilled Resource Constraints
- 17. © 2022 SPLUNK INC. Trend 2) New Roles in Security Operations Security Content Developer/ Detection Engineer Automation Engineer
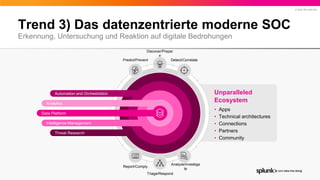
- 18. © 2022 SPLUNK INC. Trend 3) Das datenzentrierte moderne SOC Erkennung, Untersuchung und Reaktion auf digitale Bedrohungen Data Platform Intelligence Management Threat Research Analytics Automation and Orchestration Detect/Correlate Predict/Prevent Discover/Prepar e Analyze/Investiga te Report/Comply Triage/Respond Unparalleled Ecosystem • Apps • Technical architectures • Connections • Partners • Community
- 19. © 2022 SPLUNK INC. Security Product & Solution Update
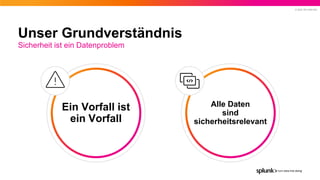
- 20. © 2022 SPLUNK INC. Unser Grundverständnis Sicherheit ist ein Datenproblem Ein Vorfall ist ein Vorfall Alle Daten sind sicherheitsrelevant
- 21. © 2022 SPLUNK INC. Das datenzentrierte moderne SOC Erkennung, Untersuchung und Reaktion auf digitale Bedrohungen Splunk Platform Threat Intelligence Management Splunk Threat Research / SURGe Splunk Enterprise Security Splunk SOAR Splunkbase • 2,700+ integrations Detect/Correlate Predict/Prevent Discover/Prepare Analyze/Investigate Report/Comply Triage/Respond
- 22. © 2022 SPLUNK INC. Splunk #1 Worldwide by Revenue in 2021 for SIEM • Splunk is the SIEM market share leader for 2021 capturing 30% of the global market • The Security market grew 23% YoY to $60B in 2021. SIEM market is now $4.1B growing 20% in 2021 • *Others = Vendors beyond the top 8 vendors in this space Chart created by Splunk based on Gartner research. Source: Gartner, Inc., Market Share: All Software Markets, Worldwide 2021; Neha Gupta; April 12, 2022. Splunk IBM Microsoft LogRhythm Micro Focus Exabeam RSA Securonix Other 30% 17% 11% 6% 5% 4% 4% 3% 21% Total Market $4.1B +20%
- 23. © 2022 SPLUNK INC. Splunk Recognized as a Leader in the 2022 Magic Quadrant for Security Information and Event Management • Splunk named a Leader for the 9th time! • One of the longest running recognitions in the history of the SIEM market. • Splunk is in the top 3 vendors for Vision and Execution in the Leaders Quadrant, moving ahead of IBM in Vision and ahead of Exabeam and Securonix in Execution Gartner disclaimer: Gartner, Inc., 2022 Magic Quadrant for Security Information and Event Management, and Critical Capabilities for Security Information and Event Management, Pete Shoard, Andrew Davies, Mitchell Schneider. 11 October 2022. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Splunk. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
- 24. © 2022 SPLUNK INC. 72.000 Leser haben abgestimmt Readers Choice PLATIN Erster Platz SIEM & SOAR
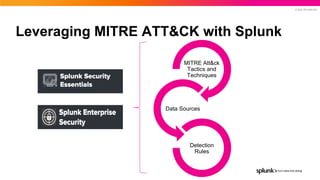
- 25. © 2022 SPLUNK INC. Leveraging MITRE ATT&CK with Splunk MITRE Att&ck Tactics and Techniques Data Sources Detection Rules
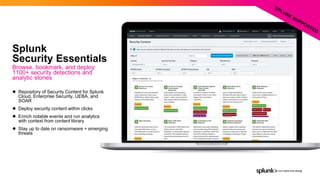
- 26. © 2022 SPLUNK INC. Splunk Security Essentials Browse, bookmark, and deploy 1100+ security detections and analytic stories ● Repository of Security Content for Splunk Cloud, Enterprise Security, UEBA, and SOAR ● Deploy security content within clicks ● Enrich notable events and run analytics with context from content library ● Stay up to date on ransomware + emerging threats
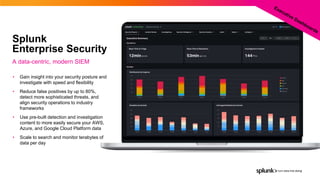
- 27. © 2022 SPLUNK INC. Splunk Enterprise Security A data-centric, modern SIEM • Gain insight into your security posture and investigate with speed and flexibility • Reduce false positives by up to 80%, detect more sophisticated threats, and align security operations to industry frameworks • Use pre-built detection and investigation content to more easily secure your AWS, Azure, and Google Cloud Platform data • Scale to search and monitor terabytes of data per day
- 28. © 2022 SPLUNK INC. Splunk Enterprise Security A data-centric, modern SIEM • Gain insight into your security posture and investigate with speed and flexibility • Reduce false positives by up to 80%, detect more sophisticated threats, and align security operations to industry frameworks • Use pre-built detection and investigation content to more easily secure your AWS, Azure, and Google Cloud Platform data • Scale to search and monitor terabytes of data per day
- 29. © 2022 SPLUNK INC. Advanced Analytics ● 700+ detections with 100+ cloud- based detections ● 30% increase in true-positive alert rates with Risk-Based Alerting (RBA) ● Enrich and prioritize alerts with integrated threat intelligence (Splunk Intelligence Management) ● Align security operations to industry frameworks (MITRE ATT&CK, NIST, CIS 20, and Kill Chain) ● Dive deep with intuitive search and investigation capabilities Boost productivity
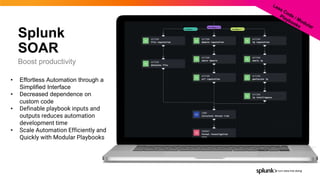
- 30. © 2022 SPLUNK INC. Splunk SOAR • Effortless Automation through a Simplified Interface • Decreased dependence on custom code • Definable playbook inputs and outputs reduces automation development time • Scale Automation Efficiently and Quickly with Modular Playbooks Boost productivity
- 31. © 2022 SPLUNK INC. Splunk SOAR • Effortless Automation through a Simplified Interface • Decreased dependence on custom code • Definable playbook inputs and outputs reduces automation development time • Scale Automation Efficiently and Quickly with Modular Playbooks Boost productivity
- 32. © 2022 SPLUNK INC. My Must Watch Sessions There are many other good once! Got Assets? Defending Your Assets Part Two: You Asked for It! SEC1219B One App To Rule Them All: Applying Machine Learning To Find Them SEC1471B Build Detection as Code Like the Splunk Threat Research Team SEC1197C Threat Research Engineer Cyber Security Unit Manager Security Engineer Senior SOAR Engineer https://conf.splunk.com/watch/conf-online.html?search=SEC1219B#/ https://conf.splunk.com/watch/conf-online.html?search=SEC1471B#/ https://conf.splunk.com/watch/conf-online.html?search=SEC1197C#/
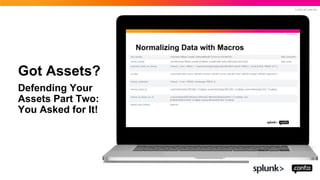
- 33. © 2022 SPLUNK INC. Got Assets? Defending Your Assets Part Two: You Asked for It!
- 34. © 2022 SPLUNK INC. Got Assets? Defending Your Assets Part Two: You Asked for It!
- 35. © 2022 SPLUNK INC. Got Assets? Defending Your Assets Part Two: You Asked for It!
- 36. © 2022 SPLUNK INC. Got Assets? Defending Your Assets Part Two: You Asked for It!
- 37. © 2022 SPLUNK INC. Got Assets? Defending Your Assets Part Two: You Asked for It!
- 38. © 2022 SPLUNK INC. Got Assets? Defending Your Assets Part Two: You Asked for It!
- 39. © 2022 SPLUNK INC. One App To Rule Them All Applying Machine Learning To Find Them
- 40. © 2022 SPLUNK INC. One App To Rule Them All Applying Machine Learning To Find Them
- 41. © 2022 SPLUNK INC. One App To Rule Them All Applying Machine Learning To Find Them
- 42. © 2022 SPLUNK INC. One App To Rule Them All Applying Machine Learning To Find Them
- 43. © 2022 SPLUNK INC. One App To Rule Them All Applying Machine Learning To Find Them
- 44. © 2022 SPLUNK INC. One App To Rule Them All Applying Machine Learning To Find Them
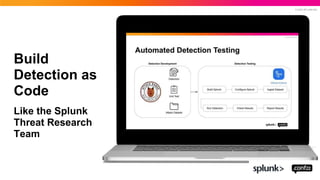
- 45. © 2022 SPLUNK INC. Build Detection as Code Like the Splunk Threat Research Team
- 46. © 2022 SPLUNK INC. Build Detection as Code Like the Splunk Threat Research Team
- 47. © 2022 SPLUNK INC. Build Detection as Code Like the Splunk Threat Research Team
- 48. © 2022 SPLUNK INC. Build Detection as Code Like the Splunk Threat Research Team
- 49. © 2022 SPLUNK INC. Build Detection as Code Like the Splunk Threat Research Team
- 50. © 2022 SPLUNK INC. Build Detection as Code Like the Splunk Threat Research Team
- 51. © 2022 SPLUNK INC. My Must Watch Sessions There are many other good once! Got Assets? Defending Your Assets Part Two: You Asked for It! SEC1219B One App To Rule Them All: Applying Machine Learning To Find Them SEC1471B Build Detection as Code Like the Splunk Threat Research Team SEC1197C Threat Research Engineer Cyber Security Unit Manager Security Engineer Senior SOAR Engineer https://conf.splunk.com/watch/conf-online.html?search=SEC1219B#/ https://conf.splunk.com/watch/conf-online.html?search=SEC1471B#/ https://conf.splunk.com/watch/conf-online.html?search=SEC1197C#/
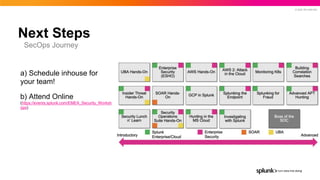
- 52. © 2022 SPLUNK INC. Next Steps SecOps Journey a) Schedule inhouse for your team! b) Attend Online (https://events.splunk.com/EMEA_Security_Worksh ops)
- 53. © 2022 SPLUNK INC. BOTS Platform https://bots.splunk.com 24x7 Access Login with Splunk.com account (just like Splunkbase) Used for all BOTS competition events More content to be added
- 54. © 2022 SPLUNK INC. Thank You!