SSL
- 2. Our Presentation Topic SSL (Secure Sockets Layer)
- 4. What is SSL? • SSL, or Secure Sockets Layer, is a means of securing communications over a network so that only the sender and receiver have access to the sensitive data that is contained within. • This is done with the use of Certificates and Keys.
- 5. Certificates and Keys • SSL, or Secure Sockets Layer, is a means of securing communications over a network so that only the sender and receiver have access to the sensitive data that is contained within. • This is done with the use of Certificates and Keys.
- 6. SSL Version • There are several versions of the SSL protocol defined. The latest version, the Transport Layer Security Protocol (TLS), is based on SSL 3.0 SSL Version 1.0 SSL Version 2.0 SSL Version 3.0 TLS Version 1.0 TLS Version 1.0 with SSL Version 3.0 compatibility
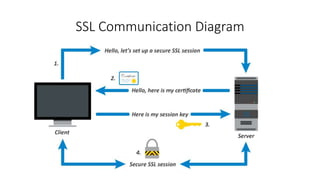
- 7. If you’ve ever bought something from Amazon, you’ve used SSL. During checkout you may have noticed the little padlock icon ( ) in the status bar of your web browser, or that the URL field of your browser begins with “https.” This is indicating that you’re communicating with the website’s server via SSL to secure your personal information, your credit card number, etc. This type of SSL between a web browser and a website server includes what is commonly referred to as Server Authentication. Example of SSL with
- 8. Server Authentication • Server Authentication is a means of authenticating and identifying the sever to the client using a Server Certificate. • A Server Certificate is a required part of any SSL communication. The server certificate contains basic information and a digital signature that properly identifies the server it is associated with.
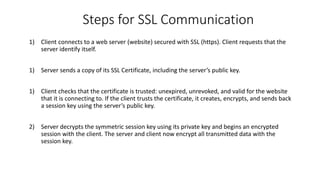
- 9. Steps for SSL Communication 1) Client connects to a web server (website) secured with SSL (https). Client requests that the server identify itself. 1) Server sends a copy of its SSL Certificate, including the server’s public key. 1) Client checks that the certificate is trusted: unexpired, unrevoked, and valid for the website that it is connecting to. If the client trusts the certificate, it creates, encrypts, and sends back a session key using the server’s public key. 2) Server decrypts the symmetric session key using its private key and begins an encrypted session with the client. The server and client now encrypt all transmitted data with the session key.
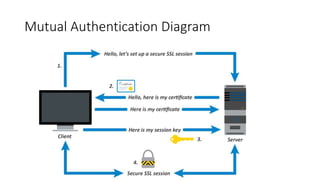
- 11. Mutual or “Two-Way” Authentication • Mutual Authentication, also commonly referred to as Two-Way Authentication, refers to the combination of both Server and Client Authentication. • The authentication is mutual, or two-way, because the server is authenticating itself to the client, and the client is authenticating itself to the server.
- 12. Client Authentication • Client Authentication, similar to server authentication, is a means of authenticating and identifying the client to the server using a Client Certificate. • A Client Certificate contains basic information about the client’s identity, and the digital signature on this certificate verifies that this information is authentic.
- 13. Steps for Mutual Authentication SSL 1) Client connects to a web server (website) secured with SSL (https). Client requests that the server identify itself. 1) Server sends a copy of its SSL Certificate, including the server’s public key. Client responds by sending a copy of its own SSL Certificate for the server to verify (This is the Mutual or Two-Way Authentication). 1) Client checks that the certificate it received is trusted: unexpired, unrevoked, and valid for the website that it is connecting to. If the client trusts the certificate, it creates, encrypts, and sends back a session key using the server’s public key. 2) Server decrypts the symmetric session key using its private key and begins an encrypted session with the client. The server and client now encrypt all transmitted data with the session key.
- 15. HOW IT WORKS Encryption of sensitive data like DES,RSA algorithm Sent between client and server through Certification like very sign
- 16. HOW IT WORKS IN BROWSER: HTTP • www.aiub.edu
- 17. HOW IT WORKS IN BROWSER: HTTPS • www.gmail.com
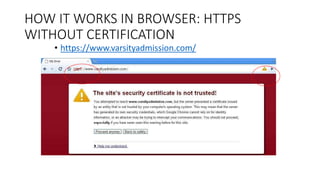
- 18. HOW IT WORKS IN BROWSER: HTTPS WITHOUT CERTIFICATION • https://www.varsityadmission.com/
- 19. HOW IT WORKS IN BROWSER: HTTPS WITHOUT CERTIFICATION
- 20. OVERALL PROCESS AND FIRST FOUR STEPS
- 21. Certificates • Web sites that deal in ecommerce must have certificates for authentication • Installed at server • Transmitted to client for authentication • Validated using CA’s public key Client machine Browser Request for secure session Server machine Web Container (JSP, ASP) Certificate signed by CA CA
- 22. Secure Socket Layer Protocol • Secure Socket Layer protocol for web communication • Latest upgrade: Transport Layer Security (TLS) • Same structure as SSL, somewhat more secure
- 23. SSL Protocol: Phase 1 Phase 1: Information exchange • Problem: Large number of encryption algorithms in use • How do client and server agree on which to use? • How does client tell server which ones it supports?
- 24. SSL Protocol: Phase 1 • Client passes preferred algorithms to server via https request • Public key encryption algorithms • Private key encryption algorithms • Hash algorithms • Compression algorithms • Also random number for key generation • Server replies with algorithms that will be used • Also passes own random number
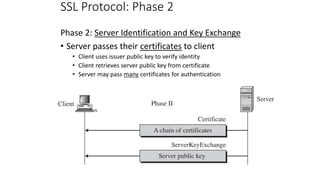
- 25. SSL Protocol: Phase 2 Phase 2: Server Identification and Key Exchange • Server passes their certificates to client • Client uses issuer public key to verify identity • Client retrieves server public key from certificate • Server may pass many certificates for authentication
- 26. SSL Protocol: Phase 2 • If no certificate containing a public key, separate public key must be passed Certificate contains RSA public key, so no separate key passed No certificate, so Diffie- Hellman key exchange parameters passed
- 27. SSL Protocol: Phase 2 • Server can also request appropriate client certificates to authenticate client • Online banking • Remote access to company database
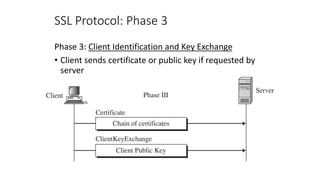
- 28. SSL Protocol: Phase 3 Phase 3: Client Identification and Key Exchange • Client sends certificate or public key if requested by server
- 29. SSL Data Transmission • Message broken into blocks • Block compressed • Compressed block hashed with authentication key to get MAC (message integrity) • Compressed block + MAC encrypted with cipher key • Encrypted block + record protocol header with version/length information sent
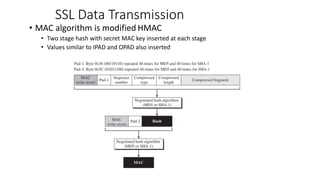
- 30. SSL Data Transmission • MAC algorithm is modified HMAC • Two stage hash with secret MAC key inserted at each stage • Values similar to IPAD and OPAD also inserted