Symantec
- 1. Critical System Protection Михаил Савушкин
- 2. Проблемы защиты серверов риски отсутствия обновлений для приложений предотвращение атак нулевого дня и целенаправленных вирусных атак контроль “неконтролируемых администраторов” неконтролируемые изменения актуальная отчетность и критерии безопасности
- 3. Как и куда лезут хакеры? Critical System Protection Enforce Registry Integrity Реестр Файлы настроек Сменные носители Enforce File Integrity Enforce Memory Protection Приложения Enforce network controls Память ОС Enforce device controls 3
- 4. Что за продукт нужен для защиты серверов? Host Intrusion Prevention • Real-Time Proactive Enforcement • Intrusion/Malware Prevention • System Hardening • Privileged User access control • Vulnerability & Patch Mitigation Host Intrusion Detection • Real-time Monitoring & Auditing • Host Intrusion Detection • File Integrity Monitoring • Configuration Monitoring • Track and Monitor user access • Logging and Event Reporting Безопаснее • Application Control
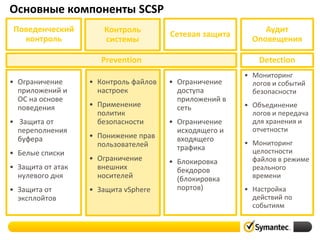
- 5. Основные компоненты SCSP Поведенческий контроль Контроль системы Сетевая защита Prevention • Ограничение приложений и ОС на основе поведения • Защита от переполнения буфера • Белые списки • Защита от атак нулевого дня • Защита от эксплойтов • Контроль файлов настроек • Применение политик безопасности • Понижение прав Re пользователей • Ограничение внешних носителей • Защита vSphere Аудит Оповещения Detection • Ограничение доступа приложений в сеть • Ограничение исходящего и входящего трафика • Блокировка бекдоров (блокировка портов) • Мониторинг логов и событий безопасности • Объединение логов и передача для хранения и отчетности • Мониторинг целостности файлов в режиме реального времени • Настройка действий по событиям
- 6. Авторизованные и неавторизованные приложения как «мостик» для компрометации системы Злоумышленник 1. 2. 3. 4. 1. 2. Хакеры и Вирусы используя уязвимости получают контроль над системой Уязвимые приложения могут запускаться с высокими правами Приложения , запущенные с правами системы или root, позволяют получить полный доступ к системе Вредоносное ПО устанавливается через доверенное приложение Сотрудник (инсайдер) устанавливает бекдор Из удаленной сети с помощью бекдора злоумышленник(сотрудник) получает доступ к системе Сотрудники
- 7. CSP использует «песочницы» для ужесточения настроек серверов Приложения Сервисы ОС Приложения … … crond RPC LPD Printer Mail Web … RSH Shell Browser Интерактивные приложения Большинство программам достаточно ограниченного доступа к ресурсам и прав Granular Resource Constraints Files НО, большинство программ имеют большие привилегии и права позволяющие атаковать систему Read/Write Data Files Registry Read Only Configuration Information Создает «песочницу» для одного или более приложений(процессов) и определяет политику поведения и доступа для данной «песочницы» Network Usage of Selected Ports and Devices Devices
- 8. Основные компоненты SCSP Поведенческий контроль Контроль системы Сетевая защита Prevention • Ограничение приложений и ОС на основе поведения • Защита от переполнения буфера • Белые списки • Защита от атак нулевого дня • Защита от эксплойтов • Контроль файлов настроек • Применение политик безопасности • Понижение прав пользователей • Ограничение внешних носителей • Защита vSphere Аудит Оповещения Detection • Ограничение доступа приложений в сеть • Ограничение исходящего и входящего трафика • Блокировка бекдоров (блокировка портов) • Мониторинг логов и событий безопасности • Объединение логов и передача для хранения и отчетности • Мониторинг целостности файлов в режиме реального времени • Настройка действий по событиям
- 9. Некорректные права пользователям- помощь злоумышленникам Злоумышленник 1. 2. 3. 1. 2. Злоумышленник или вирус получает доступ к системе Повышаются права пользователя Пользователь с завышенными правами вносит изменения в систему Зараженный сменный носитель подключается к системе сотрудниками обслуживающими систему Вирус (Stuxnet, Flamer, etc) заражает систему Сотрудники
- 10. Корректная настройка доступа к системе Злоумышленник Недоверенная пользовательская активность Ресурсы системы защищены от доступа независимо от прав пользователя Контроль системы Блокировка сменных носителей Сменные носители
- 11. Основные компоненты SCSP Поведенческий контроль Контроль системы Сетевая защита Prevention • Ограничение приложений и ОС на основе поведения • Защита от переполнения буфера • Белые списки • Защита от атак нулевого дня • Защита от эксплойтов • Контроль файлов настроек • Применение политик безопасности • Понижение прав Re пользователей • Ограничение внешних носителей • Защита vSphere Аудит Оповещения Detection • Ограничение доступа приложений в сеть • Ограничение исходящего и входящего трафика • Блокировка бекдоров (блокировка портов) • Мониторинг логов и событий безопасности • Объединение логов и передача для хранения и отчетности • Мониторинг целостности файлов в режиме реального времени • Настройка действий по событиям
- 12. Некорректная настройка межсетевого экрана Злоумышленник Credit card Source Code 1. Хакер или Вирус используюя некорректную настройку (простые гостевые пароли, настройки МСЭ итд) получает доступ к системе 2. Устанавливаются Сниферы, Кейлогеры, Бекдоры 3. Вирус используя C&C изменяет код системы и связывается с злоумышленником 4. С помощью FTP или других протоколов нужные данные из системы передаются злоумышленнику 1. Выполняет некорректную настройку МСЭ, оставляя «дыру» 2. Хакер используя дыру получает доступ к системе Администратор
- 13. Корректная настройка правил блокирует атаки Злоумышленник ATM Неавторизованная система Credit card Source Code FTP Попытка подключения записывается и блокируется Мобильный киоск Сетевая защита Попытка подключения записывается и блокируется Credit card Source Code FTP Вирус
- 14. ПРИМЕР: защита уже зараженной системы Вирус заразил систему и начал отправлять конфиденциальные данные Используется политика Targeted Prevention policy для контроля сети Соединения между системой и сетью ограниченны
- 15. Основные компоненты SCSP Поведенческий контроль Контроль системы Сетевая защита Prevention • Ограничение приложений и ОС на основе поведения • Защита от переполнения буфера • Белые списки • Защита от атак нулевого дня • Защита от эксплойтов • Контроль файлов настроек • Применение политик безопасности • Понижение прав Re пользователей • Ограничение внешних носителей • Защита vSphere Аудит Оповещения Detection • Ограничение доступа приложений в сеть • Ограничение исходящего и входящего трафика • Блокировка бекдоров (блокировка портов) • Мониторинг логов и событий безопасности • Объединение логов и передача для хранения и отчетности • Мониторинг целостности файлов в режиме реального времени • Настройка действий по событиям
- 16. CSP Detection - Мониторинг изменений конфигурации Отслеживание изменений • File and Registry Change Detection • Security Configuration Changes • Group Management Changes • Active Directory Changes • Shares Configuration Changes • Domain Trust Changes • User/Group Account Modification • Fine Grained System Activity • Malware/Spyware Detection • USB Device Activity • Monitors ESXi host configuration and VMX files 1
- 17. CSP Detection - мониторинг ключевых событий в системе System/Application Log Monitoring • Мониторинг Входа/ Выхода – Success, Failures, After Hours, Weekends, privileged user, Unusual access methods, password cracking attempts • Мониторинг Системы/Сервисов – Service/daemon/driver failures, process tracking (privileged access, unusual usage) • C2 Object Level Log Monitoring • Web Log Monitoring • Мониторинг журналов приложений – журналы Баз данных – журналы серверов приложений (например, Esxi) – журналы утилит безопасности(например, AV) – журналы Unix shell & sudo – журналы vSpehere
- 18. Использование ресурсов агентом CSP
- 19. Поддержка систем • Windows NT– Server 2012 • Solaris 8-11 • SuSE Enterprise Server 8-11 • RedHat EL 3 - 6 • AIX, HP-UX, CentOS, Oracle Linux 19
- 20. Symantec Server Protection Un-compromised at Black Hat 2011|2012|2013 Proven Security at “Capture The Flag” Challenges • Challenge: – ‘Flags hidden across un-patched Windows and Linux systems – Main flag protected with CSP and SEP out-of-the box prevention policy – 50+ skillful hackers/pen-testers from DoD, NSA, DISA, Anonymous, etc. • Attacks Techniques used: – Backtrack 5 and custom tools used during penetration attempts – Zero day attack used and stopped on protected system – Recompiled version of Flamer stopped by CSP out of the box policy • Outcome: – No one was able to capture the flag… now two years in a row… – Hackers said if they would have known that Sandboxing and Whitelisting was used, maybe not worth the time they put into it
- 22. Увеличение срока жизни Windows NT и 2000 и XP с помощью Critical System Protection • Обеспечение безопасности – Запуск только авторизованного кода на защищаемых системах • Защита от известных и неизвестных уязвимостей NT – Обеспечение защиты компонентов приложений • Снижение стоимости – Нет необходимости устанавливать патчи • Снижение рисков связанных с установкой патчей Контроль
- 23. Безопасность мобильных киосков и ATM Когда нужна надежная безопасность • Доступность 24x7 • «Легкий» агент, для снижения влияния на систему – Безопасность не должна влиять на взаимодействие с пользователем ATM Security
- 24. Безопасность мобильных киосков и ATM С помощью Critical System Protection • Безопасность – Блокировка неавторизованных приложений • Защита от вирусов и уязвимостей 0го дня • Снижение риска компрометации данных – Эффективно в «закрытых» сетях • Операционная эффективность – малое влияние на систему – Отсутствие необходимости обновлять компоненты • Снижение затрат – Уменьшение отключений устройств Контроль
- 25. Защита POS терминалов и платежных систем • POS терминалы и платежные системы подвержены атакам – Данные, используемые при покупке могут использоваться злоумышленниками • Использование уязвимых систем – Только доверенные приложения должны быть запущенны • «Легкий» агент, для снижения влияния на систему Payment Processing
- 26. Критичная инфраструктура Нуждается в реальной защите • Необходимость защиты от неавторизованного изменения – SCADA системы, медицинское оборудование итд – высокая степень надежности • «Легкий» агент, для снижения влияния на систему, отсутствие «лишних» движений – Установка патчей(ОС, приложений) может быть невозможным Критичные системы
- 27. Сервера DNS и контроллеры доменов Дополнительный подход к безопасности • Сервера с ограниченным набором специфичных приложений • Обновления антивируса, ОС, приложений могут повлечь недоступность сервисов DNS и DCS DNS и Domain Controller Servers
- 28. Защита серверов DNS и Контролеров домена С помощью Critical System Protection • Безопасность – Блокировка недоверенных приложений – Сохранение систем в состоянии «золотого» образа • Доступность – Снижение влияния на системы • без обновлений сигнатур Контроль
- 29. Защита vSphere 5.0 • Безопасность – Защита сервера vCenter , Гостевую систему – Контроль сетевого доступа и изменения компонентов vSphere • Увеличение видимости – Обеспечение мониторинга ESXi Host, Guest и vCenter • Конфигурационные файлы • Журналы(логи) vCenter Database vSphere Client vCenter Server
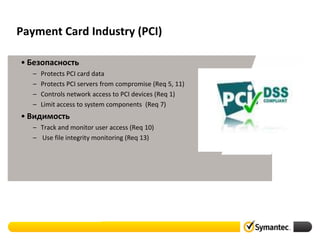
- 30. Payment Card Industry (PCI) • Безопасность – – – – Protects PCI card data Protects PCI servers from compromise (Req 5, 11) Controls network access to PCI devices (Req 1) Limit access to system components (Req 7) • Видимость – Track and monitor user access (Req 10) – Use file integrity monitoring (Req 13)
Editor's Notes
- There are several vendors that offers products to help mitigate and prevent server compromise from occurring. These types of products are usually referred to as Host Intrusion Protection (HIPS) or Host Intrusion Detection (HIDS). HIPS products can take different approach to protection systems. One approach is locking down the system to prevent unauthorized applications from getting installed (white listing). Some white listing products will only control what applications can run on the system, but does not control what the trusted application can do on the system. If the trusted application is exploited then the hacker has rights to the system. Some HIPS products monitor the wire looking for attacks targeting the system and blocking them. These products perform deep packet inspection of every packet that is coming in looking for a signature match. These types of HIPS products can only block what they know and tend to be resource hogs.HIDS products perform analysis of logs on the system looking for strings or patterns to match on. These strings and patterns are usually written to look for suspicious behavior. Some HIDS products only perform file integrity monitoring . They will monitor files on the system looking for tampering and will alert when a file has changed The vendors that are out in the market that provide these products will usually only provide one piece or they will require multiple products to provide the full range of protection Bit 9 - White listing (No Application Control) and File Integrity Monitoring only McAfee – Requires several products or licenses to perform White listing, Application Control, Configuration Monitoring and File Integrity Monitoring Trend – Provides FIM, Log Inspection and network protection CA – Provides FIM, White listing, Application Control
- CSP is one of the only products on the market that offers the best set of features to provide real time visibility and maximum control on your servers. When we break down the main features that CSP provides we can place them into several buckets (Prevention and Detection)Application Control (Prevention)When we discuss with customers the capabilities that CSP provides from a protection and prevention point of view it is important to understand how these components work. The Application Control capability of CSP uses polices to control bad behavior on the system as well as which applications can run. These polices are written to control good behavior of the applications and services that are running on the system. If an exploit occurs CSP will detect that the exploit is trying to access a resource or execute a command or modify a executable and prevent that from occurring. If I trust an application to run on the system I do not want someone to use the trust of that application to make modifications to the system. This is much different then applications that only provide white listing capabilities. White listing will control if an application can start, but once the application is started it does not control its behavior. System Control (Prevention)CSP prevention capability can also be used to lock down configuration files as well as intellectual property. This help prevent configuration drift or changes to the configuration that could result in a weaker system. CSP can also control user privileges. Even if a user has admin rights, CSP intercepts everything at the kernel level and makes a call on rather to grant that action. CSP can control access to registry, files and directories on the system as well as prevent removable drive use. Network Protection (Prevention)The network protection side of prevention can control access to and from the system based on IP and Port. The firewall does not provide deep packet inspection and does not look at any other protocols then TCP and UDP. Firewall rules can be written to control what applications are allowed to communicate and to where. Firewall rules can also be used to control when an application is communicating under what user is it allowed to make those connections. Auditing and Alerting (Detection) CSP provides file and log inspection. In Real-time CSP will monitor files for changes and will inspect log files for strings and patterns. If CSP detects a change or pattern it will send an event to the CSP MGR for logging, reporting and alerting. CSP can send out alerts via SMTP and SNMP. CSP provides out of the box queries that can be placed in reports for reporting against the data stored in the database. CSP provides a monitor tab that can be used to view and search on events in real-time.
- In most of the breaches that Verizon investigated hackers where able to infiltrate the environment hack a system and then plant a malware or malicious application on the system. When a system is hacked it is usually from a vulnerable application or brute force password attack. In either case the hacker now has privileged access to the system and can now plant a rootkit, sniffer or keylogger on the system. In all of these cases the traditional defenses (AV, IPS, Firewalls, etc) did not stop the attack. Either because these systems were looking for a specific known attack or because the hacker had a privileged user account the defense did not stop it. In other cases where breaches occurred these happened from an insider. This could either be from a disgruntled insider who knows they are about to be laid off and installs a RAT on the system or creates a privileged user account to use at a later time. Once the employee is laid off they use this to gain access back into the enviornment
- There are several products in the market place that do traditional white listing. White listing will control what applications can run but do not prevent a trusted application from doing something malicious on the system. CSP prevention policies provides least privilege application control (LPAC) to all applications running on the system. LPAC controls what applications are allowed and not allowed to do on the system. If an application attempts to access part of the system that it is not suppose to, the attempt is blocked. Certain applications will run on the system under the system or root account and will have more privileges then what is required. When these applications are exploited the hacker now has root or system access to the system and is able to make changes or install malicious applications. CSP will sandbox (confine) any sort of bad behavior from an application. If a exploit occurs against a vulnerable application and that exploit tries to access a resource or launch a command shell, LPAC will sandbox that request. CSP wraps a shim around each application and service. The shim has a set of rules that govern the behavior of that application or service. CSP can be used as a method of patch mitigation. Patches are usually installed to mitigate a vulnerability found within an application or service. These are the vulnerabilities that allow remote execution or access to resources on the system. CSP LPAC prevents application bad behavior so eliminates a vulnerable application from execution or accessing a system resource
- CSP is one of the only products on the market that offers the best set of features to provide real time visibility and maximum control on your servers. When we break down the main features that CSP provides we can place them into several buckets (Prevention and Detection)Application Control (Prevention)When we discuss with customers the capabilities that CSP provides from a protection and prevention point of view it is important to understand how these components work. The Application Control capability of CSP uses polices to control bad behavior on the system as well as which applications can run. These polices are written to control good behavior of the applications and services that are running on the system. If an exploit occurs CSP will detect that the exploit is trying to access a resource or execute a command or modify a executable and prevent that from occurring. If I trust an application to run on the system I do not want someone to use the trust of that application to make modifications to the system. This is much different then applications that only provide white listing capabilities. White listing will control if an application can start, but once the application is started it does not control its behavior. System Control (Prevention)CSP prevention capability can also be used to lock down configuration files as well as intellectual property. This help prevent configuration drift or changes to the configuration that could result in a weaker system. CSP can also control user privileges. Even if a user has admin rights, CSP intercepts everything at the kernel level and makes a call on rather to grant that action. CSP can control access to registry, files and directories on the system as well as prevent removable drive use. Network Protection (Prevention)The network protection side of prevention can control access to and from the system based on IP and Port. The firewall does not provide deep packet inspection and does not look at any other protocols then TCP and UDP. Firewall rules can be written to control what applications are allowed to communicate and to where. Firewall rules can also be used to control when an application is communicating under what user is it allowed to make those connections. Auditing and Alerting (Detection) CSP provides file and log inspection. In Real-time CSP will monitor files for changes and will inspect log files for strings and patterns. If CSP detects a change or pattern it will send an event to the CSP MGR for logging, reporting and alerting. CSP can send out alerts via SMTP and SNMP. CSP provides out of the box queries that can be placed in reports for reporting against the data stored in the database. CSP provides a monitor tab that can be used to view and search on events in real-time.
- Hackers want privileged access to a system and will either try and brute force password attack an account that is a privileged user or try and elevate a compromised user account. Once on the system hackers will attempt to make changes to the system to weaken the security, install backdoors. Resources (file, directory, network connections )are servers should be protected from unauthorized changes. Resources are the primary target of APT’s. APT will target resources in attempt to make changes to them to steal or to make use of for spreading to other systems. Over the past few years we have seen a number of malware (confiker, stuxnet, Flamer) that would use USB drives as infection points to then move from one system to another. Removable drives have also been a method that IT Ops or Service techs use to perform software updates on systems espcially systems that are not connected to the internet like ATM, POS or Plant Control systems.
- CSP prevention policy provides full control over the resources on the system. This prevents inappropriate user activity like installation unauthorized applications to someone accidently sticking an infected USB drive into the system.
- CSP is one of the only products on the market that offers the best set of features to provide real time visibility and maximum control on your servers. When we break down the main features that CSP provides we can place them into several buckets (Prevention and Detection)Application Control (Prevention)When we discuss with customers the capabilities that CSP provides from a protection and prevention point of view it is important to understand how these components work. The Application Control capability of CSP uses polices to control bad behavior on the system as well as which applications can run. These polices are written to control good behavior of the applications and services that are running on the system. If an exploit occurs CSP will detect that the exploit is trying to access a resource or execute a command or modify a executable and prevent that from occurring. If I trust an application to run on the system I do not want someone to use the trust of that application to make modifications to the system. This is much different then applications that only provide white listing capabilities. White listing will control if an application can start, but once the application is started it does not control its behavior. System Control (Prevention)CSP prevention capability can also be used to lock down configuration files as well as intellectual property. This help prevent configuration drift or changes to the configuration that could result in a weaker system. CSP can also control user privileges. Even if a user has admin rights, CSP intercepts everything at the kernel level and makes a call on rather to grant that action. CSP can control access to registry, files and directories on the system as well as prevent removable drive use. Network Protection (Prevention)The network protection side of prevention can control access to and from the system based on IP and Port. The firewall does not provide deep packet inspection and does not look at any other protocols then TCP and UDP. Firewall rules can be written to control what applications are allowed to communicate and to where. Firewall rules can also be used to control when an application is communicating under what user is it allowed to make those connections. Auditing and Alerting (Detection) CSP provides file and log inspection. In Real-time CSP will monitor files for changes and will inspect log files for strings and patterns. If CSP detects a change or pattern it will send an event to the CSP MGR for logging, reporting and alerting. CSP can send out alerts via SMTP and SNMP. CSP provides out of the box queries that can be placed in reports for reporting against the data stored in the database. CSP provides a monitor tab that can be used to view and search on events in real-time.
- Many breaches have occurred over the past because of misconfigurations on the firewall that allowed unauthorized traffic to get into the network or servers not properly being segmented. Many cases once the compromise occurred or a malware infects a system data is lifted from that system back to the hacker or to other systems. Many times servers are allowed to communicate not only on the internal network but to external systems as well without any control of who they can talk to. Many times FTP is allowed to and from these systems which allows for each extract of data.
- We have seen a lot of PCI breaches over the past few years. Where companies that are suppose to be in compliant with the digital dozen are still compromised. In many cases the system that were compromised were either not segmented from the rest of the network or allowed FTP traffic from that system to the outside world. CSP network protection can be used to segment traffic from these servers to only other authorized systems in the network as well as prevent FTP or other applications to send data to the outside world.
- Once recent use case that CSP was able to help with was a DOD customer that was breached by a malware that started sending data back to China. The customer was able to push out a policy telling the servers that they should only be talking to other systems in the same Local Subnet. This stopped the communication from these internal servers to other systems that were not on the same local subnet.
- CSP is one of the only products on the market that offers the best set of features to provide real time visibility and maximum control on your servers. When we break down the main features that CSP provides we can place them into several buckets (Prevention and Detection)Application Control (Prevention)When we discuss with customers the capabilities that CSP provides from a protection and prevention point of view it is important to understand how these components work. The Application Control capability of CSP uses polices to control bad behavior on the system as well as which applications can run. These polices are written to control good behavior of the applications and services that are running on the system. If an exploit occurs CSP will detect that the exploit is trying to access a resource or execute a command or modify a executable and prevent that from occurring. If I trust an application to run on the system I do not want someone to use the trust of that application to make modifications to the system. This is much different then applications that only provide white listing capabilities. White listing will control if an application can start, but once the application is started it does not control its behavior. System Control (Prevention)CSP prevention capability can also be used to lock down configuration files as well as intellectual property. This help prevent configuration drift or changes to the configuration that could result in a weaker system. CSP can also control user privileges. Even if a user has admin rights, CSP intercepts everything at the kernel level and makes a call on rather to grant that action. CSP can control access to registry, files and directories on the system as well as prevent removable drive use. Network Protection (Prevention)The network protection side of prevention can control access to and from the system based on IP and Port. The firewall does not provide deep packet inspection and does not look at any other protocols then TCP and UDP. Firewall rules can be written to control what applications are allowed to communicate and to where. Firewall rules can also be used to control when an application is communicating under what user is it allowed to make those connections. Auditing and Alerting (Detection) CSP provides file and log inspection. In Real-time CSP will monitor files for changes and will inspect log files for strings and patterns. If CSP detects a change or pattern it will send an event to the CSP MGR for logging, reporting and alerting. CSP can send out alerts via SMTP and SNMP. CSP provides out of the box queries that can be placed in reports for reporting against the data stored in the database. CSP provides a monitor tab that can be used to view and search on events in real-time.
- The CSP agent takes up very little memory, cpu utilization or resources on a system. The agent provides a lot of prevention and detection under a small footprint.
- Slide Objective: Demonstrate customer/industry successKey to this slide is OUT of the BOX policies!JPMC have been brought up on Whitelisting…(Cigna Cert, app signing, Bit 9….etc.)SCSP is much easier to manage than those products.Recently at the BlackHat Technical Security Conference, the Critical System Protection team set up a test allowing anyone to try their luck at retrieving a ‘flag’ hidden on an un-patched XP workstation. The goal was to have security professionals and hackers help Symantec improve the Critical System Protection product by pointing out existing gaps. The flag was secured using Critical System Protection’s out-of-the box strict prevention policies on XP un-patched workstation. The XP workstation, which had 10 known OS vulnerabilities reported by Rapid 7®, was vulnerable to attacks and had open shares that allowed external access. Hackers and pen testers from various renowned groups like the National Security Agency, Department of Defense, Defense Information Systems Agency and people who claimed to be from the Anonymous hacker group tried but failed to capture the flag.
- Because the unexpected happens in business. Change control and application control reduces the “control gap” and gets you in control of your IT infrastructure to run your business
- Because the unexpected happens in business. Change control and application control reduces the “control gap” and gets you in control of your IT infrastructure to run your business
- Because the unexpected happens in business. Change control and application control reduces the “control gap” and gets you in control of your IT infrastructure to run your business
- Because the unexpected happens in business. Change control and application control reduces the “control gap” and gets you in control of your IT infrastructure to run your business