Abstract
Ring signatures make it possible for a signer to anonymously and, yet, convincingly leak a secret by signing a message while concealing his identity within a flexibly chosen ring of users. Unlike group signatures, they do not involve any setup phase or tracing authority. Despite a lot of research efforts in more than 15 years, most of their realizations require linear-size signatures in the cardinality of the ring. In the random oracle model, two recent constructions decreased the signature length to be only logarithmic in the number N of ring members. On the downside, their suffer from rather loose reductions incurred by the use of the Forking Lemma. In this paper, we consider the problem of proving them tightly secure without affecting their space efficiency. Surprisingly, existing techniques for proving tight security in ordinary signature schemes do not trivially extend to the ring signature setting. We overcome these difficulties by combining the Groth-Kohlweiss \(\varSigma \)-protocol (Eurocrypt’15) with dual-mode encryption schemes. Our main result is a fully tight construction based on the Decision Diffie-Hellman assumption in the random oracle model. By full tightness, we mean that the reduction’s advantage is as large as the adversary’s, up to a constant factor.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
As introduced by Rivest, Shamir and Tauman [33], ring signatures make it possible for a signer to sign messages while hiding his identity within an ad hoc set of users, called a ring, that includes himself. To this end, the signer only needs to know the public keys of all ring members (besides his own secret key) in order to generate an anonymous signature on behalf of the entire ring. Unlike group signatures [16], ring signatures do not require any setup, coordination or registration phase and neither do they involve a tracing authority to de-anonymize signatures. Whoever has a public key can be appointed as a ring member without being asked for his agreement or even being aware of it. Moreover, signatures should ideally provide everlasting anonymity and carry no information as to which ring member created them. The main motivation of ring signatures is to enable the anonymous leakage of secrets, by concealing the identity of a source (e.g., a whistleblower in a political scandal) while simultaneously providing guarantees of its reliability.
In this paper, we consider the exact security of ring signatures in the random oracle model [4]. So far, the only known solutions with logarithmic signature length [24, 28] suffered from loose reductions: the underlying hard problem could only be solved with a probability smaller than the adversary’s advantage by a linear factor in the number of hash queries. Our main result is to give the first construction that simultaneously provides tight security – meaning that there is essentially no gap between the adversary’s probability of success and the reduction’s advantage in solving a hard problem – and logarithmic signature size in the number of ring members. In particular, the advantage of our reduction is not multiplicatively affected by the number \(Q_H\) of random oracle queries nor the number of \(Q_V\) of public verification keys in a ring.
Our Contribution. We describe the first logarithmic-size ring signatures with tight security proofs in the random oracle model. The unforgeability of our construction is proved under the standard Decision Diffie-Hellman (DDH) assumption in groups without a bilinear map while anonymity is achieved against unbounded adversaries. Our security proof eliminates both the linear gap in the number of random oracle queries and the \(\varTheta (Q_V)\) security loss. It thus features a fully tight reduction, meaning that – up to statistically negligible terms – the reduction’s advantage as a DDH distinguisher is only smaller than the adversary’s forging probability by a factor 2. To our knowledge, our scheme is the first ring signature for which such a fully tight reduction is reported. It is obtained by tweaking a construction due to Groth and Kohlweiss [24] and achieves tight security at the expense of increasing the number of scalars and group elements per signature by a small constant factor. For the same exact security, our reduction allows smaller key sizes which essentially decrease the signature length of [24] by a logarithmic factor n in the cardinality N of the ring and the time complexity by a factor \(\omega (n^2)\). For rings of cardinality \(N=2^6\), for example, our signatures can be 36 times faster to compute and 6 times shorter than [24].
Our Techniques. Our scheme builds on the Groth-Kohlweiss proof system [24] that allows proving that one-out-of-N commitments opens to 0 with a communication complexity \(O(\log N)\). This proof system was shown to imply logarithmic-size ring signatures with perfect anonymity assuming that the underlying commitment scheme is perfectly hiding. At the heart of the protocol of [24] is a clever use of a \(\varSigma \)-protocol showing that a committed value \(\ell \) is 0 or 1, which proceeds in the following way. In order to prove that a commitment \(\varvec{C}_\ell \in \{ \varvec{C}_i\}_{i=0}^{N-1}\) opens to 0 without revealing the index \(\ell \in \{0,\ldots ,N-1\}\), the n-bit indexes \(\ell _j\) of the binary representation \(\ell _1\ldots \ell _n \in \{0,1\}^n\) of \(\ell \in \{0,\ldots ,N-1\}\) are committed to and, for each of them, the prover uses the aforementioned \(\varSigma \)-protocol to prove that \(\ell _j \in \{0,1\}\). The response \(f_j=a_j+\ell _j x\) of the \(\varSigma \)-protocol is then viewed as a degree-one polynomial in the challenge \(x \in \mathbb {Z}_q\) and used to define polynomials
where \(f_{j,0}=f_j\) and \(f_{f,1}=x-f_j\), which have degree \(n=\log N\) if \(i=\ell \) and degree \(n-1\) otherwise. In order to prove that one of the polynomials \(\{P_i[Z]\}_{i=0}^{N-1}\) has degree n without revealing which one, Groth and Kohlweiss [24] homomorphically compute the commitment \(\prod _{i=0}^{N-1} \varvec{C}_i^{P_i(x)}\) and multiply it with \( \prod _{k=0}^{n-1} \varvec{C}_{d_k}^{-x^k}\), for auxiliary homomorphic commitments \(\{ \varvec{C}_{d_k} = \prod _{i=0}^{N-1} \varvec{C}_i^{p_{i,k}} \}_{k=0}^{n-1}\), in order to cancel out the terms of degree 0 to \(n-1\) in the exponent. Then, they prove that the product \(\prod _{i=0}^{N-1} \varvec{C}_i^{P_i(x)} \cdot \prod _{k=0}^{n-1} \varvec{C}_{d_k}^{-x^k}\) is indeed a commitment of 0. The soundness of the proof relies on the Schwartz-Zippel lemma, which ensures that \(\prod _{i=0}^{N-1} \varvec{C}_i^{P_i(x)} \cdot \prod _{k=0}^{n-1} \varvec{C}_{d_k}^{-x^k}\) is unlikely to be a commitment to 0 if \(\varvec{C}_\ell \) is not.
As an application of their proof system, Groth and Kohlweiss [24] obtained logarithmic-size ring signatures from the discrete logarithm assumption in the random oracle model. While efficient and based on a standard assumption, their scheme suffers from a loose security reduction incurred by the use of the Forking Lemma [32]. In order to extract a discrete logarithm from a ring signature forger, the adversary has to be run \(n=\log N\) times with the same random tape (where N is the ring cardinality), leading to a reduction with advantage \(\varepsilon ' \approx \frac{\varepsilon ^n}{Q_V \cdot Q_\mathcal {H}} \), where \(Q_\mathcal {H}\) is the number of hash queries and \(Q_V\) is the number of public keys. This means that, if we want to increase the key size so as to compensate for the concrete security gap, we need to multiply the security parameter by a factor \(n=\log N\), even without taking into account the factors \(Q_\mathcal {H}\) and \(Q_V\).
In our pursuit of a tight reduction, a first idea is to apply the lossy identification paradigm [2, 27] where the security proofs proceed by replacing a well-formed public key by a so-called lossy public key, with respect to which forging a signature becomes statistically impossible. In particular, the DDH-based instantiation of Katz and Wang [27] appears as an ideal candidate since, somewhat analogously to [24], well-formed public keys can be seen as homomorphic Elgamal encryptions of 0. However, several difficulties arise when we try to adapt the techniques of [2, 27] to the ring signature setting.
The first one is that the Groth-Kohlweiss ring signatures [24] rely on perfectly hiding commitments in order to achieve unconditional anonymity whereas the Elgamal encryption scheme is a perfectly binding commitment. This fortunately leaves us the hope for computational anonymity if we trade the perfectly hiding commitments for Elgamal encryptions. A second difficulty is to determine which public keys should be replaced by lossy keys in the reduction. At each public key generation query, the reduction has to decide if the newly generated key will be lossy or injective. Replacing all public keys by lossy keys is not possible because of corruptions (indeed, lossy public keys have no underlying secret key) and the reduction does not know in advance which public keys will end up in the target ring \(\mathcal {R}^\star \) of the forgery. Only replacing a randomly chosen key by a lossy key does not work either: indeed, in the ring signature setting, having one lossy public key \(PK^\dagger \) in the target ring \(\mathcal {R}^\star \) does not prevent an unbounded adversary from using the secret key of a well-formed key \(PK^\star \in \mathcal {R}^\star \setminus \{PK^\dagger \}\) to create a forgery. Moreover, as long as the reduction can only embed the challenge (injective or lossy) key in one output of the key generation oracle, it remains stuck with an advantage \(\varTheta (\varepsilon /Q_V)\) if the forger has advantage \(\varepsilon \). Arguably, this bound is the best we can hope for by directly applying the lossy identification technique.
To obtain a fully tight reduction, we depart from the lossy identification paradigm [2] in that, instead of tampering with one user’s public keys at some step, our security proof embeds a DDH instance in the public parameters \(\mathsf {pp}\) of the scheme. This allows the reduction to have all users’ private keys at disposal and reveal them to the adversary upon request. In the real system, the set \(\mathsf {pp}\) contains uniformlyrandom group elements \((g,h,\tilde{g},\tilde{h},U,V) \in \mathbb {G}^6\) and each user’s public key consists of a pair \((X,Y)=(g^\alpha \cdot h^\beta , \tilde{g}^\alpha \cdot \tilde{h}^\beta )\), where \((\alpha ,\beta ) \in \mathbb {Z}_q^2\) is the secret key. The idea of the security proof is that, if \((g,h,\tilde{g},\tilde{h}) \in \mathbb {G}^4\) is not a Diffie-Hellman tuple, the public key \(PK=(X,Y)\) uniquely determines \((\alpha ,\beta ) \in \mathbb {Z}_q^2\). In the case \(\tilde{h}=\tilde{g}^{\log _g(h)}\), the public key (X, Y) is compatible with q equally likely pairs \((\alpha ,\beta )\) since it only reveals the information \(\log _g(X)=\alpha + \log _g(h) \cdot \beta \).
The reduction thus builds a DDH distinguisher by forcing the adversary’s forgery to contain a committed encoding \(\varGamma =U^\alpha \cdot V^\beta \) of the signer’s secret key \((\alpha ,\beta ) \in \mathbb {Z}_q^2\), which can be extracted using some trapdoor information. So long as (U, V) is linearly independent of (g, h), the encoding \(\varGamma =U^\alpha \cdot V^\beta \) is independent of the adversary’s view if \((g,h,\tilde{g},\tilde{h}) \) is a Diffie-Hellman tuple. In contrast, this encoding is uniquely determined by the public key if \(\tilde{h}\ne \tilde{g}^{\log _g(h)}\). This allows the reduction to infer that \((g,h,\tilde{g},\tilde{h}) \) is a Diffie-Hellman tuple whenever it extracts \(\varGamma =U^\alpha \cdot V^\beta \) from the adversary’s forgery. To apply this argument, however, we need to make sure that signing queries do not leak any more information about \((\alpha ,\beta )\) than the public key \(PK=(X,Y)\) does. For this purpose, we resort to lossy encryption schemes [3] (a.k.a. dual-mode encryption/commitments [25, 31]), which can either behave as perfectly hiding or perfectly binding commitments depending on the distribution of the public key. In each signature, we embed a lossy encryption \((T_0,T_1)=(g^{\theta _1} \cdot h^{\theta _2} , U^\alpha \cdot V^{\beta } \cdot H_1^{\theta _1} \cdot H_2^{\theta _2} )\) of \(\varGamma =U^\alpha \cdot V^\beta \), which is computed using the DDH-based lossy encryption scheme of [3]. If \((H_1,H_2) \in \mathbb {G}^2\) is linearly independent of (g, h), then \((T_0,T_1)\) perfectly hides \(\varGamma \). At the same time, the reduction should be able to extract \(\varGamma \) from \((T_0,T_1)\) in the forgery. To combine these seemingly conflicting requirements, we derive \((H_1,H_2)\) from a (pseudo-)random oracle which is programmed to have \((H_1,H_2)=(g^\gamma ,h^\gamma )\), for some \(\gamma \in _R \mathbb {Z}_q\), in the adversary’s forgery and maintain the uniformity of all pairs \((H_1,H_2)\in \mathbb {G}^2\) in all signing queries. By doing so, the witness indistinguishability of the Groth-Kohlweiss \(\varSigma \)-protocol [24] implies that the adversary only obtains a limited amount of information from uncorrupted users’ private keys. While the above information theoretic argument is reminiscent of the security proof of Okamoto’s identification scheme [29], our proof departs from [29] in that we do not rewind the adversary as it would not enable a tight reduction.
Related Work. The concept of ring signatures was coined by Rivest, Shamir and Tauman [33] who gave constructions based on trapdoor functions and proved their security in the ideal cipher model. They also mentioned different realizations based on proofs of partial knowledge [19]. The latter approach was extended by Abe et al. [1] to support rings containing keys from different underlying signatures and assumptions. Bresson, Stern and Szydlo [11] modified the scheme of Rivest et al. [33] so as to prove it secure in the random oracle model.
In 2006, Bender, Katz and Morselli [7] provided rigorous security definitions and theoretical constructions without random oracles. In the standard model, the first efficient instantiations were put forth by Shacham and Waters [35] in groups with a bilinear map. Brakerski and Tauman-Kalai [10] gave alternative constructions based on lattice assumptions. Meanwhile, Boyen [9] suggested a generalization of the primitive with standard-model instantiations.
The early realizations [11, 33] had linear size in the cardinality of the ring. Dodis et al. [20] mentioned constant-size ring signatures as an application of their anonymous ad hoc identification protocols. However, their approach requires a setup phase where an RSA modulus is generated by some trusted entity. Chase and Lysyanskaya [15] suggested a similar construction of constant-size ring signatures from cryptographic accumulators [6]. However, efficiently instantiating their construction requires setup-free accumulators which are compatible with zero-knowledge proofs. The hash-based accumulators of [12, 13] would not provide efficient solutions as they would incur proofs of knowledge of hash function pre-images. While the lattice-based construction of [28] relies on hash-based accumulators, its security proof is not tight and its efficiency is not competitive with discrete-logarithm-based techniques. Sander’s number-theoretic accumulator [34] is an alternative candidate to instantiate [15] without a setup phase. However, it is not known to provide practical protocols: as observed in [24], it would involve much larger composite integers than standard RSA moduli (besides zero-knowledge proofs for double discrete logarithms). Moreover, it is not clear how it would be compatible with tight security proofs.
Chandran, Groth and Sahai [14] gave sub-linear-size signatures in the standard model, which were recently improved in [23]. In the random oracle model, Groth and Kohlweiss [24] described an elegant construction of logarithmic-size ring signatures based on the discrete logarithm assumption. Libert et al. [28] obtained logarithmic-size lattice-based ring signatures in the random oracle model.
The logarithmic-size ring signatures of [8, 24, 28] are obtained by applying the Fiat-Shamir heuristic [21] to interactive \(\varSigma \)-protocols. While these solutions admit security proofs under well-established assumptions in the random oracle model, their security reductions are pretty loose. In terms of exact security, they are doomed [30] to lose a linear factor in the number \(Q_\mathcal {H}\) of random oracle queries as long as they rely on the Forking Lemma [32].
The exact security of digital signatures was first considered by Bellare and Rogaway [5] and drew a lot of attention [2, 17, 22, 26, 27] since then.
2 Background
2.1 Syntax and Security Definitions for Ring Signatures
Definition 1
A ring signature scheme consists of a tuple of efficient algorithms \((\mathsf {Par}\text {-}\mathsf {Gen}, \mathsf {Keygen}, \mathsf {Sign}, \mathsf {Verify})\) with the following specifications:
-
\({\mathbf {\mathsf{{Par-Gen}}}}(1^\lambda )\) : Given a security parameter \(\lambda \), outputs the public parameters \(\mathsf {pp}\).
-
\({\mathbf {\mathsf{{Keygen}}}}(\mathsf {pp})\) : Given \(\mathsf {pp}\), outputs a key pair (PK, SK) for the user.
-
\({\mathbf {\mathsf{{Sign}}}}(\mathsf {pp}, SK, \mathcal {R}, M)\) : Given the user’s secret key SK, a ring \(\mathcal {R}\) and a message M, outputs the signature \(\sigma \) of the message M on behalf of the ring \(\mathcal {R}\).
-
\({\mathbf {\mathsf{{Verify}}}}(\mathsf {pp}, M, \mathcal {R}, \sigma )\) : Given the message M, a ring \(\mathcal {R}\) and a candidate signature \(\sigma \), the verification algorithm outputs 0 or 1.
These algorithms must also verify the correctness, meaning that for all \(\mathsf {pp} \leftarrow \textsf {Par}\text {-}\textsf {Gen}(1^\lambda )\), \((PK, SK) \leftarrow \textsf {KeyGen}(\mathsf {pp})\), for all M, and for all \(\mathcal {R}\) such that \(PK \in \mathcal {R}\), we have w.h.p \(\textsf {Verify}(\mathsf {pp}, M, \mathcal {R}, \textsf {Sign}(\mathsf {pp}, SK, \mathcal {R}, M)) = 1\).
From a security point of view, Bender et al. [7] suggested the following stringent definitions of anonymity and unforgeability.
Definition 2
A ring signature \((\mathsf {Par}\text {-}\mathsf {Gen}, \mathsf {Keygen}, \mathsf {Sign}, \mathsf {Verify})\) provides statistical anonymity under full key exposure if, for any computationally unbounded adversary \(\mathcal {A}\), there exists a negligible function \(\varepsilon (\lambda )\) such that

where \(PK_{i_0},PK_{i_1} \in \mathcal {R}^\star \) and \({\mathsf {Keygen}}\) is an oracle that generates a fresh key pair \((PK,SK) \leftarrow \mathsf {Keygen} (\mathsf {pp})\) at each query and returns both PK and SK to \(\mathcal {A}\).
Definition 3
A ring signature \((\mathsf {Par}\text {-}\mathsf {Gen}, \mathsf {Keygen}, \mathsf {Sign}, \mathsf {Verify})\) provides unforgeability w.r.t insider corruption if, for any PPT adversary \(\mathcal {A}\), there exists a negligible function \(\varepsilon (\lambda )\) such that, for any \(\mathsf {pp} \leftarrow \mathsf {Par}\text {-}\mathsf {Gen}(1^\lambda )\), we have
-
\( \mathsf {Keygen}()\): is an oracle that maintains a counter j initialized to 0. At each query, it increments j, generates \((PK_j, SK_j) \leftarrow \textsf {KeyGen}(\mathsf {pp})\) and outputs \(PK_j\).
-
\( \mathsf {Sign}(i, M ,\mathcal {R})\) is an oracle that returns \(\sigma \leftarrow \mathsf {Sign}(\mathsf {pp}, SK_i,\mathcal {R}, M)\) if \(PK_i \in \mathcal {R}\) and \((PK_i, SK_i)\) has been generated by \(\mathsf {Keygen}\). Otherwise, it returns \(\bot \).
-
\( \mathsf {Corrupt}(i)\) returns \(SK_i\) if \((PK_i, SK_i)\) was output by \({\mathsf {Keygen}}\) and \(\perp \) otherwise.
-
\(\mathcal {A}\) is restricted to output a triple \((M,\mathcal {R},\sigma )\) such that: (i) No query of the form \((\star ,M, \mathcal {R})\) has been made to \({\mathsf {Sign}(\cdot ,\cdot ,\cdot )}\); (ii) \(\mathcal {R}\) only contains public keys \(PK_i\) produced by \( {\mathsf {Keygen}}\) and for which i was never queried to \( \mathsf {Corrupt}(\cdot )\).
2.2 Hardness Assumptions
Definition 4
The Decision Diffie-Hellman (DDH) problem in \(\mathbb {G}\), is to distinguish the distributions \((g^{a},g^b,g^{ab} )\) and \((g^{a},g^b,g^{ c} )\), with  . The DDH assumption is the intractability of the problem for any PPT distinguisher.
. The DDH assumption is the intractability of the problem for any PPT distinguisher.
2.3 Reminders on \(\varSigma \)-Protocols
Definition 5
([18]). Let a prover \(\mathsf {P}\) and a verifier \(\mathsf {V}\), which are PPT algorithms, and a binary relation \(\mathcal {R}\). A protocol \((\mathsf {P}, \mathsf {V})\) is a \(\varSigma \)-protocol w.r.t. \(\mathcal {R}\), the challenge set \(\mathcal {C}\), the public input u and the private input w, if it satisfies the following:
-
3-move form: The protocol is of the following form:
-
\(\mathsf {P}\) compute commitments \(\{c_i\}_{i = 0}^j\), where \(j\in \mathbb {N}\), and sends \(\{c_i\}_{i = 0}^j\) to \(\mathsf {V}\).
-
The verifier \(\mathsf {V}\) generates a random challenge
 and sends c to \(\mathsf {P}\).
and sends c to \(\mathsf {P}\). -
The prover \(\mathsf {P}\) sends a response s to \(\mathsf {V}\).
-
On input of a transcript \((\{c_i\}_{i =0}^j, x, s)\), \(\mathsf {V}\) outputs 1 or 0.
-
-
Completeness: If \((u,w)\in \mathcal {R}\) and the prover \(\mathsf {P}\) honestly generates the transcript \((\{c_i\}_{i =0}^j, x, s)\) for a random challenge
 sent by \(\mathsf {V}\), there is a negligible function \(\varepsilon (\lambda )\) such that \(\mathsf {V}\) accepts with probability \(1-\varepsilon (\lambda )\).
sent by \(\mathsf {V}\), there is a negligible function \(\varepsilon (\lambda )\) such that \(\mathsf {V}\) accepts with probability \(1-\varepsilon (\lambda )\). -
2-Special soundness: There exists a PPT knowledge extractor \(\mathcal {E}\) that, for any public input u, on input of two accepting transcripts \((\{c_i\}_{i =0}^j, x, s)\) and \((\{c_i\}_{i =0}^j, x', s')\) with \(x \ne x'\), outputs a witness \(w'\) such that \((u, w') \in \mathcal {R}\).
-
Special Honest Verifier Zero-Knowledge (SHVZK): There is a PPT simulator \(\mathcal {S}\) that, given u and a random \(x \in \mathcal {C}\), outputs a simulated transcript \((\{c_i'\}_{i =0}^j, x, s')\) which is computationally indistinguishable from a real one.
2.4 \(\varSigma \)-protocol Showing that a Commitment Opens to 0 or 1
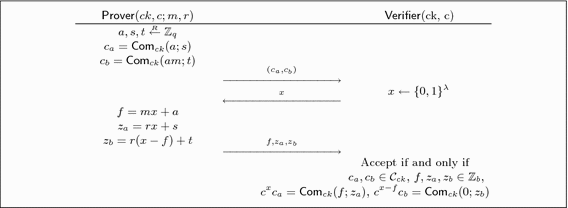
We recall the \(\varSigma \)-protocol used in [24] to prove that a commitment opens to 0 or 1. Let \( \mathcal {R} = \{(ck, c, (m, r)) \mid c = \mathsf {Com}_{ck}( m, r) ~\wedge ~( m ,r) \in \{0,1\} \times \mathbb {Z}_q\} \) the binary relation, where ck is the commitment key generated for the underlying commitment scheme, \(u=c\) is the public input and \(w=(m,r)\) is the private input. Figure 1 gives us a \(\varSigma \)-protocol \((\textsf {P}, \text {V})\) for \(\mathcal {R}\).
Theorem 1
([24, Theorem 2]). Let \((\mathsf {Setup}, \mathsf {Com})\) be a perfectly binding, computationally hiding, strongly binding and additively homomorphic commitment scheme. The \(\varSigma \)-protocol presented in Fig. 1 for the commitment to 0 or to 1 is perfectly complete, perfectly 2-special sound and perfectly SHVZK.
2.5 \(\varSigma \)-protocol for One-out-of-N Commitments Containing 0
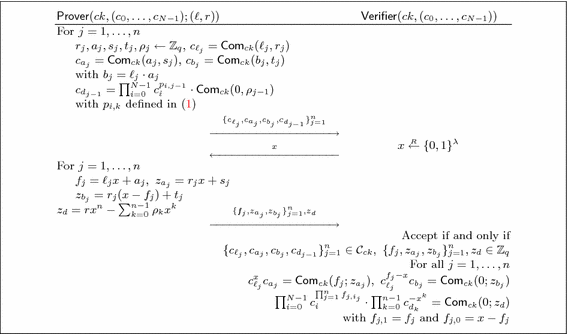
Groth and Kohlweiss [24] used the \(\varSigma \)-protocol of Sect. 2.4 to build an efficient \(\varSigma \)-protocol allowing to prove knowledge of an opening of one-out-of-N commitments \(\{ c_i \}_{i=0}^{N-1}\) to \(m=0\). Their protocol outperforms the standard OR-proof approach [19] in that its communication complexity is only \(O(\log N)\), instead of O(N). The idea is to see the responses \(f=mx+a\) of the basic \(\varSigma \) protocol as degree-1 polynomials in \(x \in \mathbb {Z}_q\) and exploit the homomorphism of the commitment.
Theorem 2
([24, Theorem 3]). The \(\varSigma \)-protocol of Fig. 2 is perfectly complete. It is (perfectly) \((n+1)\)-special sound if the commitment is (perfectly) binding. It is (perfectly) SHVZK if the commitment scheme is (perfectly) hiding.
In Fig. 2, for each i, \( p_{i,0},\ldots ,p_{i,n-1} \in \mathbb {Z}_q \) are the coefficients of the polynomial
obtained by defining \(F_{j,1} [Z]= \ell _j \cdot Z + a_j\) and \(F_{j,0}[Z]=Z-F_{j,1}[Z] \) for all \(j \in [n]\). Note that the equality (1) stems from the fact that, for each index \(i =i_1 \ldots i_n \in \{0,\ldots ,N-1\}\), we have \(F_{j,i_j}[Z]= \delta _{i_j,\ell _j} \cdot Z + (-1)^{\delta _{0,i_j}} \cdot a_j ~\) for all \(j \in [n]\), so that the coefficient of \(Z^n\) in (1) is non-zero if and only if \(i=\ell \).
2.6 A Note on the Application to Ring Signatures
In [24], Groth and Kohlweiss obtained a ring signature scheme by applying the Fiat-Shamir paradigm [21] to the above \(\varSigma \)-protocol. In short, key pairs are of the form (c, r) such that \(c=\mathsf {Com}(0;r)\) and a ring signature associated with \(\mathcal {R}=\{c_0,\ldots ,c_N\}\) is simply a proof that the signer knows how to open to 0 one of the N commitments in that ring. In [24], the following theorem states about the security of the resulting construction, denoted \((\mathsf {Setup}, \mathsf {KGen},\mathsf {Sign}, \mathsf {Vfy})\).
Theorem 3
([24, Theorem 4]). The scheme \((\mathsf {Setup}, \mathsf {KGen}, \mathsf {Sign}, \mathsf {Vfy})\) is a ring signature scheme with perfect correctness. It has perfect anonymity if the commitment scheme is perfectly hiding. It is unforgeable in the random oracle model if the commitment scheme is perfectly hiding and computationally binding.
As the security of the ring signature relies on that of the \(\varSigma \)-protocol, it is interesting to take a closer look at the computation of commitments \(\{C_{d_{j-1}}\}_{j=1}^n\) in Fig. 2. This part of the \(\varSigma \)-protocol is the only point where the ring signature generation may involve adversarially-generated values. In the anonymity game, the signer’s public key may be one of the only two honestly-generated public keys in the ring \(\mathcal {R}\). The security proof of [24] argues that, as long as the commitment is perfectly hiding, the fact that each \(C_{d_{j-1}}\) contains a (randomizing) factor \(\mathsf {Com}(0;\rho _{j-1})\), for some uniformly random \(\rho _{j-1}\), is sufficient to guarantee perfect anonymity. We point out an issue that arises when \(\mathcal {R}=\{c_0,\ldots ,c_N\}\) contains maliciously generated keys outside the space of honestly generated commitments (even if they are perfectly hiding). In short, multiplying a maliciously generated commitment by a fresh commitment may not fully “clean-up” its distribution.
The following example is a perfectly hiding commitment where re-randomizing does not wipe out maliciously generated commitments components: the setup algorithm outputs generators \(ck=(g,h)\) cyclic group \(\mathbb {G}\) of prime order q; committing to \(m\in \mathbb {Z}_q\) using randomness  is achieved by computing \( \mathsf {Com}_{ck}(m;\rho ) = (c_1,c_2,c_3)= (g^mh^r,g^s,h^s) \in \mathbb {G}^3,\) which is a perfectly hiding commitment since \(c_1\) is a Pedersen commitment and the Elgamal encryption \((c_2,c_3)\) of 0 is independent of \(c_1\). If we consider the maliciously generated commitment \((c_1^\star ,c_2^\star ,c_3^\star )=(h^u,g^v,g\cdot h^v)\), multiplying it by any \(\textsf {Com}_{ck}(0;\rho )\) does not bring it back in the range of Com. Therefore, in an instantiation with the above commitment, an unbounded adversary can defeat the anonymity property.
is achieved by computing \( \mathsf {Com}_{ck}(m;\rho ) = (c_1,c_2,c_3)= (g^mh^r,g^s,h^s) \in \mathbb {G}^3,\) which is a perfectly hiding commitment since \(c_1\) is a Pedersen commitment and the Elgamal encryption \((c_2,c_3)\) of 0 is independent of \(c_1\). If we consider the maliciously generated commitment \((c_1^\star ,c_2^\star ,c_3^\star )=(h^u,g^v,g\cdot h^v)\), multiplying it by any \(\textsf {Com}_{ck}(0;\rho )\) does not bring it back in the range of Com. Therefore, in an instantiation with the above commitment, an unbounded adversary can defeat the anonymity property.
The only missing requirement on behalf of the underlying perfectly hiding commitment is that it should be possible to efficiently recognize elements in the range of the commitment algorithm. This assumption is quite natural and satisfied by schemes like Pedersen’s commitment. Hence, this observation does not affect the perfect anonymity of the discrete-log-based instantiation of [24].
3 A Fully Tight Construction from the DDH Assumption
We modify the scheme of [24] so as to prove its unforgeability via a fully tight reduction from the DDH assumption. The advantage of the DDH distinguisher is only smaller than the adversary’s advantage by a (small) constant factor.
The price to pay for this fully tight reduction is relatively small since signatures are only longer than in [24] by roughly 2n group elements. Moreover, as in [24], our signing algorithm requires \(\varTheta (N)\) exponentiations if N is the size of the ring.
3.1 Description
We exploit the fact that, in the \(\varSigma \)-protocol of [24], not all first-round messages should be computed using the same commitment scheme as the one used to compute the public key. The second step of the signing algorithm computes perfectly hiding commitments \(\{ \varvec{C}_{d_k}\}_{k=0}^{n-1}\) which are vectors of dimension 4. They live in a different space than public keys \((X,Y)=(g^{\alpha } \cdot h^\beta , \tilde{g}^\alpha \cdot \tilde{h}^\beta )\), which are DDH-based lossy encryptions of (and thus perfectly hiding commitments to) 0.
The signer generates a commitment \((T_0,T_1)=(g^{\theta _1} \cdot h^{\theta _2}, \varGamma \cdot H_1^{\theta _1} \cdot H_2^{\theta _2} )\) to \(\varGamma =U^{\alpha _\ell } \cdot V^{\beta _\ell }\), which encodes his secret key \((\alpha _\ell ,\beta _\ell ) \in \mathbb {Z}_q^2\). This defines a vector \(\varvec{V}_{\ell }=(X_{\ell },Y_{\ell },T_0,T_1) \in \mathbb {G}^4\) in the column space of a matrix \(\mathbf {M}_H \in \mathbb {G}^{4 \times 4}\), which has full rank in the scheme but not in the proof of unforgeability. Then, for each key \(\varvec{X}_i=(X_i,Y_i)\) in the ring \(\mathcal {R}\), the signer defines \(\varvec{V}_i=(X_i,Y_i,T_0,T_1)^\top \in \mathbb {G}^4\) and, by extending the technique of [24], generates a NIZK proof that one of the vectors \(\{ \varvec{V}_i \}_{i=0}^{N-1}\) is in the column span of \(\mathbf {M}_H\). To prove this without revealing which \(\varvec{V}_{\ell } \in \mathbb {G}^4\) is used, the commitments \(\{\varvec{C}_{d_{j-1}} \}_{j=1}^n\) are re-randomized by multiplying them with a random vector in the column space of \(\mathbf {M}_H\).
-
\({\mathbf {\mathsf{{Par-Gen}}}}(1^\lambda )\) : Given a security parameter \(\lambda \), choose a cyclic group \(\mathbb {G}\) of prime order q with generators
 and
and  . Choose hash functions \(\mathcal {H}_{\mathsf {FS}} : \{0,1\}^*\rightarrow \mathbb {Z}_q\) and \(\mathcal {H}:\{0,1\}^*\rightarrow \mathbb {G}^2\) which will be modeled as random oracles. Output the common public parameters \(\mathsf {pp}=\bigl ( \lambda , \mathbb {G},g,h,\tilde{g},\tilde{h},U,V \bigr ).\)
. Choose hash functions \(\mathcal {H}_{\mathsf {FS}} : \{0,1\}^*\rightarrow \mathbb {Z}_q\) and \(\mathcal {H}:\{0,1\}^*\rightarrow \mathbb {G}^2\) which will be modeled as random oracles. Output the common public parameters \(\mathsf {pp}=\bigl ( \lambda , \mathbb {G},g,h,\tilde{g},\tilde{h},U,V \bigr ).\)
-
\({\mathbf {\mathsf{{Keygen}}}}(\mathsf {pp})\) : Given \(\mathsf {pp}\), choose a secret key is
 and compute the public key \(PK=\varvec{X}=(X,Y)=(g^\alpha \cdot h^\beta ,\tilde{g}^\alpha \cdot \tilde{h}^\beta )\).
and compute the public key \(PK=\varvec{X}=(X,Y)=(g^\alpha \cdot h^\beta ,\tilde{g}^\alpha \cdot \tilde{h}^\beta )\). -
\({\mathbf {\mathsf{{Sign}}}}(\mathsf {pp},SK,\mathcal {R},M)\) : To sign \(M \in \{0,1\}^*\) on behalf of \(\mathcal {R}=\{\varvec{X}_0,\ldots ,\varvec{X}_{N-1}\} \) such that \(\varvec{X}_i=(X_i,Y_i) \in \mathbb {G}^2\) for each \(i \in [N]\), the signer uses \(SK= (\alpha ,\beta ) \) and \(PK=\varvec{X}=(X,Y)=(g^\alpha \cdot h^\beta ,\tilde{g}^\alpha \cdot \tilde{h}^\beta ) \in \mathcal {R}\) as follows. We assume that \(N=2^n\) for some n. Let \(\ell \in \{0,\ldots ,N-1\}\) the index of \(PK=\varvec{X}\) in \(\mathcal {R} \) when \(\mathcal {R}\) is arranged in lexicographical order and write it as \(\ell = \ell _1 \ldots \ell _n \in \{0,1\}^n\).
-
1.
Choose
 . For all \(j \in [n]\), choose
. For all \(j \in [n]\), choose  and compute \((T_0,T_1) = \big ( g^{\theta _1} \cdot h^{\theta _2}, U^{\alpha } \cdot V^{\beta } \cdot H_1^{\theta _1} \cdot H_2^{\theta _2} \big )\), as well as $$\begin{aligned} \nonumber \varvec{C}_{\ell _j}= & {} ( {C}_{\ell _j,0}, {C}_{\ell _j,1}) = \big ( g^{r_j} \cdot h^{s_j}, ~g^{\ell _j} \cdot H_1^{r_j} \cdot H_2^{s_j} \big ) \\ \varvec{C}_{a_j}= & {} ( {C}_{a_j,0}, {C}_{a_j,1}) = \big ( g^{t_j} \cdot h^{u_j}, ~g^{a_j} \cdot H_1^{t_j} \cdot H_2^{u_j} \big ) \\ \nonumber \varvec{C}_{b_j}= & {} ( {C}_{b_j,0}, {C}_{b_j,1}) = \big ( g^{v_j} \cdot h^{w_j}, ~g^{\ell _j \cdot a_j} \cdot H_1^{v_j} \cdot H_2^{w_j} \big ), \end{aligned}$$(2)
and compute \((T_0,T_1) = \big ( g^{\theta _1} \cdot h^{\theta _2}, U^{\alpha } \cdot V^{\beta } \cdot H_1^{\theta _1} \cdot H_2^{\theta _2} \big )\), as well as $$\begin{aligned} \nonumber \varvec{C}_{\ell _j}= & {} ( {C}_{\ell _j,0}, {C}_{\ell _j,1}) = \big ( g^{r_j} \cdot h^{s_j}, ~g^{\ell _j} \cdot H_1^{r_j} \cdot H_2^{s_j} \big ) \\ \varvec{C}_{a_j}= & {} ( {C}_{a_j,0}, {C}_{a_j,1}) = \big ( g^{t_j} \cdot h^{u_j}, ~g^{a_j} \cdot H_1^{t_j} \cdot H_2^{u_j} \big ) \\ \nonumber \varvec{C}_{b_j}= & {} ( {C}_{b_j,0}, {C}_{b_j,1}) = \big ( g^{v_j} \cdot h^{w_j}, ~g^{\ell _j \cdot a_j} \cdot H_1^{v_j} \cdot H_2^{w_j} \big ), \end{aligned}$$(2)where \((H_1,H_2)= \mathcal {H}\big ( M,\mathcal {R}, T_0, \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big ) \in \mathbb {G}^2\). Define
$$\begin{aligned} \mathbf {M}_H= & {} \begin{bmatrix} ~~g~~&~~h~~&~1~&~1~ \\ \tilde{g}&\tilde{h}&1&1 \\ 1&1&g&h \\ ~U~&~V~&~H_1~&~H_2~ \end{bmatrix} \in \mathbb {G}^{4 \times 4} \end{aligned}$$(3)and its corresponding discrete logarithms \({\mathbf {L}}_h = \log _g( \mathbf {M}_H)\) matrix
$$\begin{aligned} {\mathbf {L}}_h= & {} \begin{bmatrix} ~~1~~&~~\log _g(h)~~&~0~&~0~ \\ \log _g(\tilde{g})&\log _g(\tilde{h})&0&0 \\ 0&0&1&\log _g(h) \\ ~\log _g(U)~&~\log _g(V)~&~\log _g(H_1)~&~\log _g(H_2)~ \end{bmatrix} \in \mathbb {Z}_q^{4 \times 4}. \end{aligned}$$(4)Note that the signer’s witnesses \((\alpha ,\beta ,\theta _1,\theta _2) \in \mathbb {Z}_q^4\) satisfy
$$\begin{aligned} \log _g \begin{bmatrix} X \mid Y \mid T_0 \mid T_1 \end{bmatrix}^\top= & {} {\mathbf {L}}_h \cdot \begin{bmatrix} \alpha \mid \beta \mid \theta _1 \mid \theta _2 \end{bmatrix}^\top . \end{aligned}$$(5)In the following, we will sometimes re-write relation (5) as
$$\begin{aligned} \begin{bmatrix} X \\ Y \\ T_0 \\ T_1 \end{bmatrix}= & {} \begin{bmatrix} ~~g~~&~~h~~&~1~&~1~ \\ \tilde{g}&\tilde{h}&1&1 \\ 1&1&g&h \\ ~U~&~V~&~H_1~&~H_2~ \end{bmatrix} \odot \begin{bmatrix} \alpha \\ \beta \\ \theta _1 \\ \theta _2 \end{bmatrix}. \end{aligned}$$(6)For each \(i \in [N]\), define the vector \(\varvec{V}_i = ( X_i, Y_i, T_0, T_1 )^\top \in \mathbb {G}^4\). The next step is to prove knowledge of witnesses \((\alpha _\ell ,\beta _\ell ,\theta _1,\theta _2) \in \mathbb {Z}_q^4\) such that \(\varvec{V}_\ell = ( X_\ell , Y_\ell , T_0 , T_1 )^\top = g^{\mathbf {L}_h \cdot (\alpha _\ell ,\beta _\ell ,\theta _1,\theta _2)^\top } \), for some \( \ell \in [N]\).
-
2.
For each \(j \in [n]\), pick
 and compute $$\begin{aligned} \varvec{C}_{d_{j-1}} = \prod _{i=0}^{N-1} \varvec{V}_i^{p_{i,j-1}} \cdot g^{ \mathbf {L}_h \cdot (\rho _{j-1,\alpha }, \rho _{j-1,\beta },\rho _{j-1,\theta _1}, \rho _{j-1,\theta _2} )^\top } ~~ \in \mathbb {G}^4, \quad \end{aligned}$$(7)
and compute $$\begin{aligned} \varvec{C}_{d_{j-1}} = \prod _{i=0}^{N-1} \varvec{V}_i^{p_{i,j-1}} \cdot g^{ \mathbf {L}_h \cdot (\rho _{j-1,\alpha }, \rho _{j-1,\beta },\rho _{j-1,\theta _1}, \rho _{j-1,\theta _2} )^\top } ~~ \in \mathbb {G}^4, \quad \end{aligned}$$(7)where, for each \(i \in \{0,\ldots ,N-1\}\), \(p_{i,0},\ldots ,p_{i,n-1} \) are the coefficients of
$$\begin{aligned} P_i[Z] = \prod _{j=1}^n F_{j,i_j} [Z] = \delta _{i,\ell } \cdot Z^n + \sum _{k=0}^{n-1} p_{i,k} \cdot Z^k ~\in \mathbb {Z}_q[Z],\quad \end{aligned}$$(8)where \(F_{j,1} [Z]= \ell _j \cdot Z + a_j\) and \(F_{j,0}[Z]=Z-F_{j,1}[Z] \) for all \(j \in [n]\). Note that the coefficient of \(Z^n\) in (8) is non-zero if and only if \(i=\ell \).
-
3.
Compute \(x=\mathcal {H}_{\mathsf {FS}}(M,\mathcal {R}, T_0,T_1, \{ \varvec{C}_{\ell _j} , \varvec{C}_{a_j} , \varvec{C}_{b_j} , \varvec{C}_{d_{j-1}} \}_{j=1}^n ) ~\in \mathbb {Z}_q \).
-
4.
For each \(j \in [n]\), compute (modulo q) \(f_j = \ell _j \cdot x + a_j =F_{j,1}(x)\) and
$$\begin{aligned} z_{r_j}= & {} r_j \cdot x + t_j , \quad \qquad \qquad ~ \bar{z}_{r_j} = r_j \cdot (x-f_j) + v_j \\ z_{s_j}= & {} s_j \cdot x + u_j , \quad \qquad \qquad \bar{z}_{s_j} = s_j \cdot (x -f_j) + w_j \end{aligned}$$and
$$\begin{aligned} z_{d,\alpha }= & {} \alpha \cdot x^n - \sum _{k=0}^{n-1} \rho _{k,\alpha } \cdot x^k, \qquad ~~~ z_{d,\beta } = \beta \cdot x^n - \sum _{k=0}^{n-1} \rho _{k,\beta } \cdot x^k \\ z_{d,\theta _1}= & {} \theta _1 \cdot x^n - \sum _{k=0}^{n-1} \rho _{k,\theta _1} \cdot x^k, \qquad ~ z_{d,\theta _2} = \theta _2 \cdot x^n - \sum _{k=0}^{n-1} \rho _{k,\theta _2} \cdot x^k \end{aligned}$$
Let \(\mathbf {\Sigma }_j=\big (\varvec{C}_{\ell _j}, \varvec{C}_{a_j},\varvec{C}_{b_j}, \varvec{C}_{d_{j-1}}, f_j,z_{r_j},z_{s_j},\bar{z}_{r_j},\bar{z}_{s_j} \big ) \) for all \(j \in [n]\) and output
$$\begin{aligned} \sigma =\bigl ( \{ \mathbf {\Sigma }_j \}_{j=1}^n, T_0,T_1, z_{d,\alpha },z_{d,\beta },z_{d,\theta _1},z_{d,\theta _2} \bigr ). \qquad \end{aligned}$$(9) -
1.
-
\({\mathbf {\mathsf{{Verify}}}}(\mathsf {pp}, M, \mathcal {R},\sigma )\) : Given a ring \(\mathcal {R}=\{\varvec{X}_0,\ldots ,\varvec{X}_{N-1}\} \) and a pair \((M,\sigma )\), parse \(\sigma \) as in (9) and define \(f_{j,1}=f_j\) and \(f_{j,0} = x-f_j\) for each \(j \in [n]\).
-
1.
Compute \((H_1,H_2)= \mathcal {H}\big (M,\mathcal {R}, T_0, \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big ) \in \mathbb {G}^2\) and, for each public key \(\varvec{X}_i=(X_i,Y_i) \in \mathbb {G}^2\) in \(\mathcal {R}\), set \(\varvec{V}_i = ( X_i , Y_i , T_0 , T_1 )^\top \in ~\mathbb {G}^4\).
-
2.
Let \(x= \mathcal {H}_{\mathsf {FS}}(M,\mathcal {R}, T_0,T_1, \{ \varvec{C}_{\ell _j}, \varvec{C}_{a_j}, \varvec{C}_{b_j}, \varvec{C}_{d_{j-1}} \}_{j=1}^n ) \). If the equalities
$$\begin{aligned} {\varvec{C}}_{a_j} \cdot \varvec{C}_{\ell _j}^{ x}= & {} \big ( g^{z_{r_j}} \cdot h^{z_{s_j}}, ~g^{f_j} \cdot H_1^{z_{r_j}} \cdot H_2^{z_{s_j}} \big ),\\ \nonumber {\varvec{C}}_{b_j} \cdot \varvec{C}_{\ell _j}^{x-f_j}= & {} \big ( g^{\bar{z}_{r_j}} \cdot h^{\bar{z}_{s_j}}, H_1^{\bar{z}_{r_j}} \cdot H_2^{\bar{z}_{s_j}} \big ), \qquad \qquad \forall j \in [n] \end{aligned}$$(10)are not satisfied, return 0. Then, return 1 if and only if
$$\begin{aligned}&\prod _{i=0}^{N-1} \varvec{V}_i^{\prod _{j=1}^n f_{j,i_j}} \cdot \prod _{j=1}^n \varvec{C}_{d_{j-1}}^{-(x^{j-1})} \nonumber \\&\qquad = \begin{bmatrix} ~~g~~&~~h~~&~1~&~1~ \\ \tilde{g}&\tilde{h}&1&1 \\ 1&1&g&h \\ ~U~&~V~&~H_1~&~H_2~ \end{bmatrix} \odot \begin{bmatrix} z_{d,\alpha } \\ z_{d,\beta } \\ z_{d,\theta _1} \\ z_{d,\theta _2} \end{bmatrix}. \qquad \qquad \end{aligned}$$(11)
-
1.
Correctness is shown by observing from (8) that \(\prod _{i=0}^{N-1} \varvec{V}_i^{\prod _{j=1}^n f_{j,i_j}} \) equals
where the last equality follows from (7). Since \(\varvec{V}_\ell = g^{\mathbf {L}_h \cdot (\alpha _\ell ,\beta _\ell ,\theta _1,\theta _2)^\top } \), we obtain
3.2 Security Proofs
Statistical anonymity is achieved because \(\{\varvec{C}_{d_{j-1}}\}_{j=1}^n\) are uniformly distributed. The reason is that the matrices (4) have full rank in the scheme (but not in the proof of unforgeability), so that computing \(\varvec{C}_{d_{j-1}}\) as per (7) makes its distribution uniform over \(\mathbb {G}^4\). The proof of Theorem 4 is given in the full version of the paper.
Theorem 4
Any unbounded anonymity adversary \(\mathcal {A}\) has advantage at most \( \mathbf {Adv}_\mathcal {A}^{\mathrm {anon}}(\lambda ) \le \frac{2}{q} + \frac{Q_{\mathcal {H}_\mathsf {FS}}}{q^2}, \) where \(Q_{\mathcal {H}_{\mathsf {FS}}}\) is the number of hash queries to \(\mathcal {H}_{\mathsf {FS}}\).
Theorem 5
The scheme is unforgeable under the DDH assumption in the random oracle model. For any adversary \(\mathcal {A}\) with running time t and making \(Q_V\) queries to the key generation oracle, \(Q_S\) signing queries as well as \(Q_\mathcal {H}\) and \(Q_{\mathcal {H}_{\mathsf {FS}}}\) queries to the random oracles \(\mathcal {H}\) and \(\mathcal {H}_{\mathsf {FS}}\), respectively, there is a DDH distinguisher \(\mathcal {B}\) with running time \(t' \le t + \mathsf {poly}(\lambda ,Q_S,Q_V,Q_\mathcal {H})\) and such that
Proof
We use a sequence of games where, for each i, \(W_i\) stands for the event that the challenger outputs 1 in Game i.
-
Game 0: This is the real game. At each query \(i \in [Q_V]\) to the key generation oracle \(\mathsf {Keygen}(\cdot )\), the challenger \(\mathcal {B}\) honestly chooses
 and returns the public key \(PK_i=\varvec{X}_i=(X_i,Y_i)=(g^{\alpha _i} \cdot h^{\beta _i},\tilde{g}^{\alpha _i} \cdot \tilde{h}^{\beta _i})\) and retains \(SK_i=(\alpha _i,\beta _i)\) for later use. If \(\mathcal {A}\) subsequently submits \(\varvec{X}_i=(X_i,Y_i)\) to the corruption oracle, \(\mathcal {B}\) reveals \(SK_i=(\alpha _i,\beta _i)\). Moreover, all signing queries are answered by faithfully running the signing algorithm. At the end of the game, \(\mathcal {A}\) outputs a forgery \((M^\star ,\sigma ^\star ,\mathcal {R}^\star )\), where \(\mathcal {R}^\star =\{ \varvec{X}_0^\star ,\ldots ,\varvec{X}_{N^\star -1}^\star \}\), $$\begin{aligned} \sigma ^\star =\bigl ( \{ \mathbf {\Sigma }_j^\star \}_{j=1}^n , T_0^\star ,T_1^\star , z_{d,\alpha }^\star ,z_{d,\beta }^\star ,z_{d,\theta _1}^\star ,z_{d,\theta _2}^\star \bigr ) , \qquad \end{aligned}$$(13)
and returns the public key \(PK_i=\varvec{X}_i=(X_i,Y_i)=(g^{\alpha _i} \cdot h^{\beta _i},\tilde{g}^{\alpha _i} \cdot \tilde{h}^{\beta _i})\) and retains \(SK_i=(\alpha _i,\beta _i)\) for later use. If \(\mathcal {A}\) subsequently submits \(\varvec{X}_i=(X_i,Y_i)\) to the corruption oracle, \(\mathcal {B}\) reveals \(SK_i=(\alpha _i,\beta _i)\). Moreover, all signing queries are answered by faithfully running the signing algorithm. At the end of the game, \(\mathcal {A}\) outputs a forgery \((M^\star ,\sigma ^\star ,\mathcal {R}^\star )\), where \(\mathcal {R}^\star =\{ \varvec{X}_0^\star ,\ldots ,\varvec{X}_{N^\star -1}^\star \}\), $$\begin{aligned} \sigma ^\star =\bigl ( \{ \mathbf {\Sigma }_j^\star \}_{j=1}^n , T_0^\star ,T_1^\star , z_{d,\alpha }^\star ,z_{d,\beta }^\star ,z_{d,\theta _1}^\star ,z_{d,\theta _2}^\star \bigr ) , \qquad \end{aligned}$$(13)with \(\mathbf {\Sigma }_j^\star = \big ( \varvec{C}_{\ell _j}^\star , \varvec{C}_{a_j}^\star ,\varvec{C}_{b_j}^\star , \varvec{C}_{d_{j-1}}^\star , f_j^\star ,z_{r_j}^\star ,z_{s_j}^\star ,\bar{z}_{r_j}^\star ,\bar{z}_{s_j}^\star \big ) \). At this point, \(\mathcal {B}\) outputs 1 if and only if \(\mathcal {A}\) wins, meaning that: (i) \(\sigma ^\star \) correctly verifies; (ii) \(\mathcal {R}^\star \) only contains uncorrupted public keys; (iii) No signing query involved a tuple of the form \((\cdot ,M^\star ,\mathcal {R}^\star )\). By definition, we have \(\mathbf {Adv}^{\mathrm {euf-cma}}_\mathcal {A}(\lambda ) = \Pr [W_0]\).
-
Game 1: This game is like Game 0 but we modify the signing oracle. Note that each signing query triggers a query to the random oracle \(\mathcal {H}(.)\) since the challenger \(\mathcal {B}\) has to faithfully compute \(T_0\) and \( \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n\) before obtaining \(\mathcal {H}\big (M,\mathcal {R}, T_0 , \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big )\). In Game 1, at each signing query, \(\mathcal {B}\) aborts in the event that \(\mathcal {H}(\cdot )\) was already defined for the input \(\big (M,\mathcal {R}, T_0 , \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big )\). Since such an input contains uniformly random elements, the probability to abort during the entire game is at most \(Q_S \cdot (Q_S + Q_\mathcal {H})/q^2\) and we have \(|\Pr [W_1]-\Pr [W_0]| \le Q_S \cdot (Q_S+ Q_\mathcal {H})/q^2\).
-
Game 2: We modify the random oracle \(\mathcal {H}\) when it is directly invoked by \(\mathcal {A}\) (i.e., \(\mathcal {H}\)-queries triggered by signing queries are treated as in Game 0). At each \(\mathcal {H}\)-query \(\big (M,\mathcal {R}, T_0 , \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big )\), the challenger \(\mathcal {B}\) returns the previously defined value if it exists. Otherwise, it picks
 and defines the hash value as \((H_1,H_2)=\mathcal {H}\big (M,\mathcal {R}, T_0 , \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big ) =(g^\gamma ,h^\gamma ).\) Note that \(\mathcal {H}(\cdot )\) is no longer a truly random oracle since \((g,h,H_1,H_2)\) is a Diffie-Hellman tuple. Still, under the DDH assumption, this modification has no noticeable effect on \(\mathcal {A}\)’s winning probability. Lemma 1 describes a DDH distinguisher such that \(|\Pr [W_2]-\Pr [W_1]| \le \mathbf {Adv}^{\mathrm {DDH}}_\mathcal {B}(\lambda ) + 1/q\).
and defines the hash value as \((H_1,H_2)=\mathcal {H}\big (M,\mathcal {R}, T_0 , \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big ) =(g^\gamma ,h^\gamma ).\) Note that \(\mathcal {H}(\cdot )\) is no longer a truly random oracle since \((g,h,H_1,H_2)\) is a Diffie-Hellman tuple. Still, under the DDH assumption, this modification has no noticeable effect on \(\mathcal {A}\)’s winning probability. Lemma 1 describes a DDH distinguisher such that \(|\Pr [W_2]-\Pr [W_1]| \le \mathbf {Adv}^{\mathrm {DDH}}_\mathcal {B}(\lambda ) + 1/q\).
Since \((g,h,H_1,H_2)\) is a Diffie-Hellman tuple in Game 2, \(\gamma \in \mathbb {Z}_q \) can be used as a decryption key for the DDH-based dual-mode encryption scheme. Another consequence of the last transition is that the matrix \(\mathbf {L}_h\) of (3) has no longer full rank since its last row is linearly dependent with the first three rows.
-
Game 3: We introduce a failure event \(F_3\) which causes the challenger \(\mathcal {B}\) to output 0. When \(\mathcal {A}\) outputs its forgery \(\sigma ^\star \), \(\mathcal {B}\) parses \(\sigma ^\star \) as in (13) and computes \((H_1^\star ,H_2^\star )=\mathcal {H}\big ( M^\star ,\mathcal {R}^\star , T_0^\star , \{ {C}_{\ell _j,0}^\star ,{C}_{a_j,0}^\star ,{C}_{b_j,0}^\star \}_{j=1}^n \big )\). Event \(F_3\) is defined to be the event that either: (1) The hash value \((H_1^\star ,H_2^\star )\) was not defined at any time; (2) It was defined but collides with a pair \((H_1,H_2)=\mathcal {H}\big (M,\mathcal {R}, T_0 , \{ {C}_{\ell _j,0},{C}_{a_j,0},{C}_{b_j,0} \}_{j=1}^n \big )\) defined in response to a signing query \((\ell ,M,\mathcal {R})\) for some index \(\ell \in \{0,\ldots , |\mathcal {R}|-1\}\), when \(\mathcal {R}\) is arranged in lexicographic order. Note that the probability of case (1) cannot exceed 1 / q because \(\mathcal {H}(\cdot ) \) is unpredictable as a random oracle. Moreover, since a winning adversary must forge a signature on some \((M^\star ,\mathcal {R}^\star )\) that has never been queried for signature, the probability of case (2) is bounded by \(Q_S/q^2\) multiplied by \(Q_\mathcal {H}\) since we must consider the probability that a tuple \((g,h,H_1,H_2)\) defined in a signing query is accidentally a Diffie-Hellman tuple and collides with the response of a hash query. We find \(|\Pr [W_3]-\Pr [W_2]| \le \Pr [F_3] \le 1/q+ Q_S\cdot Q_\mathcal {H}/q^2 \).
-
Game 4: This game is identical to Game 3 with one modification. When the adversary \(\mathcal {A}\) outputs its forgery \(\sigma ^\star \), \(\mathcal {B}\) parses \(\sigma ^\star \) as in (13) and computes \((H_1^\star ,H_2^\star )=\mathcal {H}\big ( M^\star ,\mathcal {R}^\star , T_0^\star , \{ {C}_{\ell _j,0}^\star ,{C}_{a_j,0}^\star ,{C}_{b_j,0}^\star \}_{j=1}^n \big )\). Then, \(\mathcal {B}\) recalls the previously defined exponent \(\gamma ^\star \in \mathbb {Z}_q\) such that \((H_1^\star ,H_2^\star )=(g^{\gamma ^\star } ,h^{\gamma ^\star })\) and uses it to decrypt the dual-mode ciphertexts \(\{ \varvec{C}_{\ell _j}^\star \}_{j=1}^n\). It aborts and outputs 0 if one of these ciphertexts turns out not to encrypt a bit \(\ell _j^\star \in \{0,1\}\). Note that, if \(\mathcal {B}\) does not abort, it decodes an n-bit string \(\ell ^\star =\ell _1^\star \ldots \ell _n^\star \in \{0,1\}^n \) from \(\{ \varvec{C}_{\ell _j}^\star \}_{j=1}^n\). We claim that we have \(|\Pr [W_4]-\Pr [W_3]| \le (1+ Q_{\mathcal {H}_\mathsf {FS}})/q \).
The only situation where Game 4 deviates from Game 3 is the event \(F_4\) that either: (i) \(\mathcal {A}\) did not query \(\mathcal {H}_{\mathsf {FS}}( \cdot )\) on the input that the forgery relates to; (ii) \(\mathcal {A}\) manages to break the soundness of the proof system showing that each of the ciphertexts \(\{ \varvec{C}_{\ell _j}^\star \}_{j=1}^n\) encrypts a bit. Lemma 2 shows that \(\Pr [F_4] \le (1+ Q_{\mathcal {H}_\mathsf {FS}})/q\).
-
Game 5: In this game, we modify the challenger’s behavior when \(\mathcal {A}\) outputs a forgery \(\sigma ^\star \). Having decoded the n-bit string \(\ell ^\star =\ell _1^\star \ldots \ell _n^\star \in \{0,1\}^n \) from the dual-mode ciphertexts \(\{ \varvec{C}_{\ell _j}^\star \}_{j=1}^n\), \(\mathcal {B}\) also runs the decryption algorithm for \((T_0^\star ,T_1^\star )\) to compute \(\varGamma ^\star = T_1^\star /{T_0^\star }^{\gamma ^\star }\). At this point, \(\mathcal {B}\) recalls the secret key \(SK=(\alpha _{\ell ^\star },\beta _{\ell ^\star })\) of the \(\ell ^\star \)-th member of the ring \(\mathcal {R}^\star =\{ \varvec{X}_0^\star , \ldots \varvec{X}_{N^\star -1}^\star \}\) in lexicographical order. If \(\varGamma ^\star =U^{\alpha _{\ell ^\star }} \cdot V^{\beta _{\ell ^\star }}\), \(\mathcal {B}\) outputs 1. Otherwise, it outputs 0. Lemma 3 shows that \(|\Pr [W_5]-\Pr [W_4]| \le Q_{\mathcal {H}_\mathsf {FS}} \cdot \log (Q_V) /q\).
-
Game 6: This game is identical to Game 5 except that we change the distribution of \(\mathsf {pp}=\bigl ( \lambda , \mathbb {G},g,h,\tilde{g},\tilde{h},U,V \bigr )\). Here, instead of choosing
 uniformly, we set \((g,h,\tilde{g},\tilde{h})=(g,h,g^\rho ,h^\rho )\) for a randomly chosen
uniformly, we set \((g,h,\tilde{g},\tilde{h})=(g,h,g^\rho ,h^\rho )\) for a randomly chosen  . Clearly, the two distributions of \(\mathsf {pp}\) are indistinguishable under the DDH assumption and \(\mathcal {B}\) can immediately be turned into an efficient DDH distinguisher (the proof is straightforward) such that \(| \Pr [W_6]-\Pr [W_5]| \le \mathbf {Adv}_\mathcal {B}^{\mathrm {DDH}}(\lambda )\).
. Clearly, the two distributions of \(\mathsf {pp}\) are indistinguishable under the DDH assumption and \(\mathcal {B}\) can immediately be turned into an efficient DDH distinguisher (the proof is straightforward) such that \(| \Pr [W_6]-\Pr [W_5]| \le \mathbf {Adv}_\mathcal {B}^{\mathrm {DDH}}(\lambda )\). -
Game 7: This game is like Game 6 except that we now simulate the proof of knowledge of secret keys in all outputs of the signing oracle. On a signing query \((M,\mathcal {R},\ell )\), where (\(0 \le \ell \le |\mathcal {R}|-1\)), the challenger parses \(\mathcal {R}\) as \(\{\varvec{X}_0,\ldots ,\varvec{X}_{N-1} \}\) and returns \(\perp \) if \(\varvec{X}_{\ell }\) is not public keys produced by the \(\mathsf {Keygen}(.)\) oracle. Otherwise, the challenger chooses
 as well as
as well as  and
and  , for all \(j \in [n]\). Then, it picks
, for all \(j \in [n]\). Then, it picks  as well as
as well as  for all \(j \in [n]\), and honestly computes \({C}_{\ell _j,0}=g^{r_j}\cdot h^{s_j}\) for all \(j \in [n]\). It can now compute for all \(j\in [n]\), $$\begin{aligned} {{C}}_{a_j,0}&= g^{z_{r_j}} \cdot h^{z_{s_j}} \cdot {C}_{\ell _j,0}^{-x} ,&{{C}}_{b_j,0}&= g^{\bar{z}_{r_j}} \cdot h^{\bar{z}_{s_j}} \cdot {C}_{\ell _j,0}^{f_j-x} , \end{aligned}$$
for all \(j \in [n]\), and honestly computes \({C}_{\ell _j,0}=g^{r_j}\cdot h^{s_j}\) for all \(j \in [n]\). It can now compute for all \(j\in [n]\), $$\begin{aligned} {{C}}_{a_j,0}&= g^{z_{r_j}} \cdot h^{z_{s_j}} \cdot {C}_{\ell _j,0}^{-x} ,&{{C}}_{b_j,0}&= g^{\bar{z}_{r_j}} \cdot h^{\bar{z}_{s_j}} \cdot {C}_{\ell _j,0}^{f_j-x} , \end{aligned}$$and define \((H_1,H_2)=\mathcal {H}(M,\mathcal {R},T_0,\{({C}_{\ell _j,0},{{C}}_{a_j,0},{{C}}_{b_j,0})\}_{j=1}^n)\). Then, it completes the computation of dual-mode commitments as follows. First, it chooses
 and computes \({C}_{\ell _j,1}=g^{\ell _j}\cdot H_1^{r_j} \cdot H_2^{s_j}\) for all \(j\in [n]\). Then, it computes $$\begin{aligned} {{C}}_{a_j,1}&= \big ( g^{f_j} \cdot H_1^{z_{r_j}} \cdot H_2^{z_{s_j}} \big ) \cdot {C}_{\ell _j,1}^{-x} ,&{{C}}_{b_j,1}&= \big ( H_1^{\bar{z}_{r_j}} \cdot H_2^{\bar{z}_{s_j}} \big ) \cdot {C}_{\ell _j,1}^{f_j-x} , \end{aligned}$$
and computes \({C}_{\ell _j,1}=g^{\ell _j}\cdot H_1^{r_j} \cdot H_2^{s_j}\) for all \(j\in [n]\). Then, it computes $$\begin{aligned} {{C}}_{a_j,1}&= \big ( g^{f_j} \cdot H_1^{z_{r_j}} \cdot H_2^{z_{s_j}} \big ) \cdot {C}_{\ell _j,1}^{-x} ,&{{C}}_{b_j,1}&= \big ( H_1^{\bar{z}_{r_j}} \cdot H_2^{\bar{z}_{s_j}} \big ) \cdot {C}_{\ell _j,1}^{f_j-x} , \end{aligned}$$for all \(j\in [n]\). Then, for each \(j\in \{2,\ldots ,n\}\), the challenger faithfully computes \({\varvec{C}}_{d_{j-1}}\) as per (7) but, for index \(j=1\), it computes
$$\begin{aligned} {\varvec{C}}_{d_0} = \prod _{i=0}^{N-1} \varvec{V}_i^{\prod _{j=1}^n f_{j,i_j}} \prod _{j=2}^n {\varvec{C}}_{d_{j-1}}^{-(x^{j-1})} \Bigl ( \mathbf {M}_\mathcal {H}\odot (-z_{d,\alpha },-z_{d, \beta },-z_{d,\theta _1},-z_{d,\theta _2})^\top \Bigr ) , \end{aligned}$$where \(\varvec{V}_i=(X_i,Y_i,T_0,T_1)^\top \), \(f_{j,1}=f_j\) and \(f_{j,0} = x-f_j\) for each \(j \in [n]\). Finally, the challenger \(\mathcal {B}\) programs the random oracle \(\mathcal {H}_\mathsf {FS}\) to have the equality \(x=\mathcal {H}_\mathsf {FS}(M,\mathcal {R},T_0,T_1, \{ \varvec{C}_{\ell _j} , {\varvec{C}}_{a_j} , {\varvec{C}}_{b_j} , \varvec{C}_{d_{j-1}} \}_{j=1}^n ) \). If \(\mathcal {H}_\mathsf {FS}\) was already defined for this input, \(\mathcal {B}\) aborts and outputs 0. If the simulation does not fail, the oracle sets \(\mathbf {\Sigma }_j= \big ( \varvec{C}_{\ell _j} , \varvec{C}_{a_j},\varvec{C}_{b_j}, \varvec{C}_{d_{j-1}}, f_j, z_{r_j},z_{s_j},\bar{z}_{r_j},\bar{z}_{s_j} \big )\) for all \(j \in [n]\) and outputs the signature \( \sigma =\bigl ( \{ \mathbf {\Sigma }_j \}_{j=1}^n , T_0,T_1, z_{d,\alpha },z_{d, \beta },z_{d,\theta _1}, z_{d,\theta _2} \bigr ) ,\) which is distributed exactly as in Game 6 unless \((g,h,H_1,H_2)\) happens to form a Diffie-Hellman tuple. Indeed, although the adversary’s signing queries may involve rings \(\mathcal {R}\) that contain maliciously generated keys of the form \(\varvec{X}_i=(X_i,Y_i)=(X_i,\varOmega _i \cdot X_i^{\log _g(\tilde{g})})\), with \(\varOmega _i \ne 1_\mathbb {G}\), this does not prevent the simulated commitments \(\{\varvec{C}_{d_{j-1}}\}_{j=1}^n\) from having the same distribution as in Game 6. In simulated signatures, we indeed have
$$\begin{aligned} \varvec{C}_{d_{j-1}}= & {} \prod _{i=0}^{N-1} \varvec{V}_i^{p_{i,j-1}} \cdot g^{\mathbf {L}_h \cdot \varvec{\rho }_{j}} \qquad \quad \forall j \in \{2,\ldots ,n-1\} \end{aligned}$$for random \(\varvec{\rho }_{2},\ldots , \varvec{\rho }_{n-1} \in _R \mathbb {Z}_q^4\), where \(p_{i,0},\ldots ,p_{i,n-1}\) are the coefficients of \(\prod _{j=1}^n f_{j,i_j} = \delta _{i,\ell } x^n + \sum _{j=1}^n p_{i,j-1} x^{j-1}\). Since \(\varvec{V}_\ell = g^{\mathbf {L}_h \cdot (\alpha _\ell ,\beta _\ell ,\theta _1,\theta _2)^\top }\) and defining \(\varvec{\rho }_1=- (z_{d,\alpha },z_{d,\beta },z_{d,\theta _1},z_{d,\theta _1})^\top - \sum _{j=2}^{n} \varvec{\rho }_j x^{j-1} + ({\alpha }_{\ell } ,{\beta }_{\ell },\theta _1,\theta _2 ) \cdot x^n,\) we have
$$\begin{aligned} \varvec{C}_{d_0}= & {} \varvec{V}_{\ell }^{x^n } \cdot \prod _{i=0 }^{N-1} \varvec{V}_i^{ \sum _{j=1}^n p_{i,j-1} x^{j-1} } \cdot \prod _{i=0}^{N-1} \varvec{V}_i^{-\sum _{j=2}^n p_{i,j-1} x^{j-1}} \\&\qquad \cdot \,\,g^{-\mathbf {L}_h \cdot (z_{d,\alpha },z_{d,\beta },z_{d,\theta _1},z_{d,\theta _1})^\top -\mathbf {L}_h \cdot \sum _{j=2}^{n} \varvec{\rho }_{j} x^{j-1} } = \prod _{i=0 }^{N-1} \varvec{V}_i^{ p_{i,0} } \cdot g^{ \mathbf {L}_h \cdot \varvec{\rho }_{1} } \end{aligned}$$Note that the Fiat-Shamir proof does not hide which index \(\ell \in \{0,1\}^n\) the signing oracle uses (and it does not have to since \(\mathcal {A}\) knows \(\ell \)): indeed, for any signing query, the matrix \(\mathbf {L}_h\) has only rank 3 and \(\varvec{X}_{\ell }\) may be the only key of the ring \(\mathcal {R}\) to be in the column span of \(\mathbf {M}_H\). However, the same holds in Game 6. As long as the simulation does not fail because of a collision on \(\mathcal {H}_{\mathsf {FS}}\) or because \((H_1,H_2)\) accidentally lands in the span of (g, h) at some signing query, the simulated proof is perfectly indistinguishable from a real proof that would be generated as in Game 6. Taking into account the probability that the signing oracle fails at some query, we obtain the inequality \(|\Pr [W_7] - \Pr [W_6] | \le Q_S/q + Q_{S} \cdot (Q_{\mathcal {H}_{\mathsf {FS}}} + Q_S)/q^2\).
In Game 7, we claim that \(\Pr [W_7]= 2/q\). To prove this claim, we recall that \(\mathcal {B}\) only outputs 1 if \((T_0^\star ,T_1^\star )\) decrypts to \(\varGamma ^\star =U^{\alpha _{\ell ^\star }} \cdot V^{\beta _{\ell ^\star }}\). We next argue that, except with probability 1 / q, \( \varGamma ^\star \) is independent of \(\mathcal {A}\)’s view in Game 7.
Indeed, since \((g,h,\tilde{g},\tilde{h})\) is a Diffie-Hellman tuple, the only information that \(\varvec{X}_{\ell ^\star }= (X_{\ell ^\star },Y_{\ell ^\star })= (g^{\alpha _{\ell ^\star } }\cdot h^{\beta _{\ell ^\star }} , \tilde{g}^{\alpha _{\ell ^\star } } \cdot \tilde{h}^{\beta _{\ell ^\star }})\) reveals about \((\alpha _{\ell ^\star },\beta _{\ell ^\star }) \in \mathbb {Z}_q^2\) is \(\log _g( X_{\ell ^\star } ) = \alpha _{\ell ^\star } + \log _g (h) \cdot \beta _{\ell ^\star } \) since \(\log _g( Y_{\ell ^\star } ) \) only provides redundant information. Also, in all outputs of the signing oracle, the pair  is chosen independently of \(U^{\alpha _{\ell ^\star }} \cdot V^{\alpha _{\ell ^\star }}\). Finally, in Game 7, all signing queries are answered by simulating a NIZK proof without using the witnesses \(SK_{\ell ^\star }=(\alpha _{\ell ^\star },\beta _{\ell ^\star }) \in \mathbb {Z}_q^2\) at any time. This ensures that no information is leaked about \((\alpha _{\ell ^\star },\beta _{\ell ^\star })\) whatsoever.
is chosen independently of \(U^{\alpha _{\ell ^\star }} \cdot V^{\alpha _{\ell ^\star }}\). Finally, in Game 7, all signing queries are answered by simulating a NIZK proof without using the witnesses \(SK_{\ell ^\star }=(\alpha _{\ell ^\star },\beta _{\ell ^\star }) \in \mathbb {Z}_q^2\) at any time. This ensures that no information is leaked about \((\alpha _{\ell ^\star },\beta _{\ell ^\star })\) whatsoever.
Taking into account the event that (U, V) accidentally falls in the span of (g, h), we find that \( \varGamma ^\star \) remains independent of \(\mathcal {A}\)’s view until the forgery stage. In this case, \((T_0^\star ,T_1^\star )\) only decrypts to \(U^{\alpha _{\ell ^\star }} \cdot V^{\beta _{\ell ^\star }}\) with probability 1 / q, which implies \(\Pr [W_7]= 2 /q\). When counting probabilities, we obtain the bound (12). \(\square \)
Lemma 1
There exists an efficient DDH distinguisher \(\mathcal {B}\) that bridges between Game 1 and Game 2 and such that \(|\Pr [W_2]-\Pr [W_1] | \le \mathbf {Adv}^{\mathrm {DDH}}_\mathcal {B}(\lambda )+ 1/q\).
Proof
We consider a DDH instance \((g,g^a,g^b,g^{ab+c})\) for which \(\mathcal {B}\) has to decide if \(c=0\) or \(c\in _R \mathbb {Z}_q\). To do this, \(\mathcal {B}\) initially defines \(h=g^b\) and emulates the random oracle \(\mathcal {H}( \cdot )\) at each (direct) query by randomly choosing  and setting \((H_1,H_2) = \big ( (g^a)^{\delta _1} \cdot g^{\delta _2} , (g^{ab+c})^{\delta _1 } \cdot (g^b)^{\delta _2} \big ) = \big ( g^{a \delta _1 +\delta _2} , g^{(a \delta _1 +\delta _2)b + c \delta _1} \big ) \). If \(c=0\), \((H_1,H_2)\) is distributed as in Game 2 for \(\gamma =a \delta _1 + \delta _2\). If \(c \in _R \mathbb {Z}_q\), we have \(c \ne 0\) with probability \(1-1/q\), so that \((H_1,H_2)\) are uniform over \(\mathbb {G}^2\) and independently distributed across distinct queries, exactly as in Game 1. When \(\mathcal {A}\) halts, \(\mathcal {B}\) outputs 1 if \(\mathcal {A}\) creates a valid forgery and 0 otherwise. \(\square \)
and setting \((H_1,H_2) = \big ( (g^a)^{\delta _1} \cdot g^{\delta _2} , (g^{ab+c})^{\delta _1 } \cdot (g^b)^{\delta _2} \big ) = \big ( g^{a \delta _1 +\delta _2} , g^{(a \delta _1 +\delta _2)b + c \delta _1} \big ) \). If \(c=0\), \((H_1,H_2)\) is distributed as in Game 2 for \(\gamma =a \delta _1 + \delta _2\). If \(c \in _R \mathbb {Z}_q\), we have \(c \ne 0\) with probability \(1-1/q\), so that \((H_1,H_2)\) are uniform over \(\mathbb {G}^2\) and independently distributed across distinct queries, exactly as in Game 1. When \(\mathcal {A}\) halts, \(\mathcal {B}\) outputs 1 if \(\mathcal {A}\) creates a valid forgery and 0 otherwise. \(\square \)
Lemma 2
From Game 3 to Game 4, the adversary’s winning probabilities differ by at most \(|\Pr [W_4] - \Pr [W_3]| \le (1+Q_{\mathcal {H}_{\mathsf {FS}}})/ q \).
Proof
We bound the probability \(\Pr [F_4]\). Recall that \(F_4\) occurs if \(\mathcal {A}\) breaks the soundness of the proof that a dual-mode ciphertext encrypts a bit. This implies that \( \sigma ^\star =\bigl ( \{ \mathbf {\Sigma }_j^\star \}_{j=1}^n , T_0^\star ,T_1^\star , z_{d,\alpha }^\star , z_{d,\beta }^\star , z_{d,\theta _1}^\star , z_{d,\theta _2}^\star \bigr ) \) verifies and there exists \(k \in [ n] \) such that \(\mathbf {\Sigma }_k^\star = (\varvec{C}_{\ell _k}^\star , \varvec{C}_{a_k}^\star , \varvec{C}_{b_k}^\star , \varvec{C}_{d_{k-1}^\star }, f_k^\star ,z_{r_k}^\star , z_{s_k}^\star , \bar{z}_{r_k}^\star , \bar{z}_{s_k}^\star ) \) contains a ciphertext \(\varvec{C}_{\ell _k}^\star \) that decrypts to \(\ell _k \not \in \{0,1\}\). For this index k, \(\sigma ^\star \) contains a NIZK proof
that \(\varvec{C}_{\ell _k}^\star \) encrypts \(\ell _k^\star \in \{0,1\}\). This proof, which is obtained from the \(\varSigma \)-protocol of [24, Fig. 1], is known [24, Theorem 2] to provide special soundness with soundness error 1 / q. Hence, if the statement is false and \(\varvec{C}_{\ell _k}^\star \) does not encrypt a bit, for any given pair \((\varvec{C}_{a_k}^\star , \varvec{C}_{b_k}^\star )\), only one challenge value \(x \in \mathbb {Z}_q\) admits a response \((f_k^\star ,z_{r_k}^\star , z_{s_k}^\star , \bar{z}_{r_k}^\star , \bar{z}_{s_k}^\star )\) that makes (14) into an accepting transcript.
At each query \(\mathcal {H}_{\mathsf {FS}}(M,\mathcal {R}, T_0,T_1, \{ \varvec{C}_{\ell _j} , \varvec{C}_{a_j} , \varvec{C}_{b_j} , {\varvec{C}}_{d_{j-1}} \}_{j=1}^n )\) such that one of the \(\{ \varvec{C}_{\ell _j}\}_{j=1} \) does not encrypt a binary value, the probability that oracle \(\mathcal {H}_{\mathsf {FS}}(\cdot )\) returns the unique “bad" \(x \in \mathbb {Z}_q\) for which a correct response exists is exactly 1 / q. Finally, since \(\mathcal {H}_{\mathsf {FS}}\) is simulated by the challenger \(\mathcal {B}\), we may assume that \(\mathcal {B}\) makes the query \(\mathcal {H}_{\mathsf {FS}}(M^\star ,\mathcal {R}^\star , T_0^\star ,T_1^\star , \{ \varvec{C}_{\ell _j}^\star , \varvec{C}_{a_j}^\star , \varvec{C}_{b_j}^\star , \varvec{C}_{d_{j-1}}^\star \}_{j=1}^n )\) for itself in case it was not explicitly made by the time \(\mathcal {A}\) terminates. Taking a union bound over all \(\mathcal {H}_{\mathsf {FS}}\)-queries, we obtain \(|\Pr [W_4] - \Pr [W_3]| \le \Pr [F_4] \le (1+ Q_{\mathcal {H}_{\mathsf {FS}}})/ q\). \(\square \)
Lemma 3
From Game 4 to Game 5, the adversary’s winning probabilities differ by at most \(|\Pr [W_5]-\Pr [W_4]| \le Q_{\mathcal {H}_\mathsf {FS}} \cdot \log (Q_V) /q\). (The proof is Appendix B.1.)
References
Abe, M., Ohkubo, M., Suzuki, K.: 1-out-of-n signatures from a variety of keys. In: Zheng, Y. (ed.) ASIACRYPT 2002. LNCS, vol. 2501, pp. 415–432. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-36178-2_26
Abdalla, M., Fouque, P.-A., Lyubashevsky, V., Tibouchi, M.: Tightly-secure signatures from lossy identification schemes. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 572–590. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_34
Bellare, M., Hofheinz, D., Yilek, S.: Possibility and impossibility results for encryption and commitment secure under selective opening. In: Joux, A. (ed.) EUROCRYPT 2009. LNCS, vol. 5479, pp. 1–35. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-01001-9_1
Bellare, M., Rogaway, P.: Random oracles are practical: a paradigm for designing efficient protocols. In: ACM CCS (1993)
Bellare, M., Rogaway, P.: The exact security of digital signatures-how to sign with RSA and Rabin. In: Maurer, U. (ed.) EUROCRYPT 1996. LNCS, vol. 1070, pp. 399–416. Springer, Heidelberg (1996). https://doi.org/10.1007/3-540-68339-9_34
Benaloh, J., de Mare, M.: One-way accumulators: a decentralized alternative to digital signatures. In: Helleseth, T. (ed.) EUROCRYPT 1993. LNCS, vol. 765, pp. 274–285. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48285-7_24
Bender, A., Katz, J., Morselli, R.: Ring signatures: stronger definitions, and constructions without random oracles. In: Halevi, S., Rabin, T. (eds.) TCC 2006. LNCS, vol. 3876, pp. 60–79. Springer, Heidelberg (2006). https://doi.org/10.1007/11681878_4
Bootle, J., Cerulli, A., Chaidos, P., Ghadafi, E., Groth, J., Petit, C.: Short accountable ring signatures based on DDH. In: Pernul, G., Ryan, P.Y.A., Weippl, E. (eds.) ESORICS 2015. LNCS, vol. 9326, pp. 243–265. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-24174-6_13
Boyen, X.: Mesh signatures. In: Naor, M. (ed.) EUROCRYPT 2007. LNCS, vol. 4515, pp. 210–227. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-72540-4_12
Brakerski, Z., Tauman-Kalai, Y.: A framework for efficient signatures, ring signatures and identity based encryption in the standard model. Cryptology ePrint Archive: Report 2010/086 (2010)
Bresson, E., Stern, J., Szydlo, M.: Threshold ring signatures and applications to ad-hoc groups. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 465–480. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45708-9_30
Buldas, A., Laud, P., Lipmaa, H.: Accountable certificate management using undeniable attestations. In: ACM-CCS (2000)
Camacho, P., Hevia, A., Kiwi, M., Opazo, R.: Strong accumulators from collision-resistant hashing. In: Wu, T.-C., Lei, C.-L., Rijmen, V., Lee, D.-T. (eds.) ISC 2008. LNCS, vol. 5222, pp. 471–486. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-85886-7_32
Chandran, N., Groth, J., Sahai, A.: Ring signatures of sub-linear size without random oracles. In: Arge, L., Cachin, C., Jurdziński, T., Tarlecki, A. (eds.) ICALP 2007. LNCS, vol. 4596, pp. 423–434. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-73420-8_38
Chase, M., Lysyanskaya, A.: On signatures of knowledge. In: Dwork, C. (ed.) CRYPTO 2006. LNCS, vol. 4117, pp. 78–96. Springer, Heidelberg (2006). https://doi.org/10.1007/11818175_5
Chaum, D., van Heyst, E.: Group signatures. In: Davies, D.W. (ed.) EUROCRYPT 1991. LNCS, vol. 547, pp. 257–265. Springer, Heidelberg (1991). https://doi.org/10.1007/3-540-46416-6_22
Coron, J.-S.: On the exact security of full domain hash. In: Bellare, M. (ed.) CRYPTO 2000. LNCS, vol. 1880, pp. 229–235. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-44598-6_14
Cramer, R.: Modular design of secure, yet practical cryptographic protocols. Ph.D. thesis, University of Amsterdam (1996)
Cramer, R., Damgård, I., Schoenmakers, B.: Proofs of partial knowledge and simplified design of witness hiding protocols. In: Desmedt, Y.G. (ed.) CRYPTO 1994. LNCS, vol. 839, pp. 174–187. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48658-5_19
Dodis, Y., Kiayias, A., Nicolosi, A., Shoup, V.: Anonymous identification in Ad Hoc groups. In: Cachin, C., Camenisch, J.L. (eds.) EUROCRYPT 2004. LNCS, vol. 3027, pp. 609–626. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-24676-3_36
Fiat, A., Shamir, A.: How to prove yourself: practical solutions to identification and signature problems. In: Odlyzko, A.M. (ed.) CRYPTO 1986. LNCS, vol. 263, pp. 186–194. Springer, Heidelberg (1987). https://doi.org/10.1007/3-540-47721-7_12
Goh, E.-J., Jarecki, S.: A signature scheme as secure as the Diffie-Hellman problem. In: Biham, E. (ed.) EUROCRYPT 2003. LNCS, vol. 2656, pp. 401–415. Springer, Heidelberg (2003). https://doi.org/10.1007/3-540-39200-9_25
González, A.: A ring signature of size \(O(\root 3 \of {n})\) without random oracles. Cryptology ePrint Archive: Report 2017/905 (2017)
Groth, J., Kohlweiss, M.: One-out-of-many proofs: or how to leak a secret and spend a coin. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. LNCS, vol. 9057, pp. 253–280. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46803-6_9
Groth, J., Sahai, A.: Efficient non-interactive proof systems for bilinear groups. In: Smart, N. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 415–432. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-78967-3_24
Kakvi, S.A., Kiltz, E.: Optimal security proofs for full domain hash, revisited. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 537–553. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_32
Katz, J., Wang, N.: Efficiency improvements for signature schemes with tight security reductions. In: ACM-CCS (2003)
Libert, B., Ling, S., Nguyen, K., Wang, H.: Zero-knowledge arguments for lattice-based accumulators: logarithmic-size ring signatures and group signatures without trapdoors. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016. LNCS, vol. 9666, pp. 1–31. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49896-5_1
Okamoto, T.: Provably secure and practical identification schemes and corresponding signature schemes. In: Brickell, E.F. (ed.) CRYPTO 1992. LNCS, vol. 740, pp. 31–53. Springer, Heidelberg (1993). https://doi.org/10.1007/3-540-48071-4_3
Paillier, P., Vergnaud, D.: Discrete-log-based signatures may not be equivalent to discrete log. In: Roy, B. (ed.) ASIACRYPT 2005. LNCS, vol. 3788, pp. 1–20. Springer, Heidelberg (2005). https://doi.org/10.1007/11593447_1
Peikert, C., Vaikuntanathan, V., Waters, B.: A framework for efficient and composable oblivious transfer. In: Wagner, D. (ed.) CRYPTO 2008. LNCS, vol. 5157, pp. 554–571. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-85174-5_31
Pointcheval, D., Stern, J.: Security proofs for signature schemes. In: Maurer, U. (ed.) EUROCRYPT 1996. LNCS, vol. 1070, pp. 387–398. Springer, Heidelberg (1996). https://doi.org/10.1007/3-540-68339-9_33
Rivest, R.L., Shamir, A., Tauman, Y.: How to leak a secret. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 552–565. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-45682-1_32
Sander, T.: Efficient accumulators without trapdoor extended abstract. In: Varadharajan, V., Mu, Y. (eds.) ICICS 1999. LNCS, vol. 1726, pp. 252–262. Springer, Heidelberg (1999). https://doi.org/10.1007/978-3-540-47942-0_21
Shacham, H., Waters, B.: Efficient ring signatures without random oracles. In: Okamoto, T., Wang, X. (eds.) PKC 2007. LNCS, vol. 4450, pp. 166–180. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-71677-8_12
Acknowledgements
This work was funded in part by the French ANR ALAMBIC project (ANR-16-CE39-0006).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A Reminders on Commitment Schemes
A non-interactive commitment scheme allows a sender to commit to a message m by sending a commitment string to the receiver. Later on the sender can convince the receiver that the committed value was really m. A commitment scheme must satisfy two security properties called hiding and binding. The former captures that the commitment hides any partial information about the message. The latter requires that the sender be unable to open the commitment to two distinct messages. Formally, a non-interactive commitment scheme is a pair of PPT algorithms \((\mathsf {Setup}, \mathsf {Com})\). The setup algorithm \(ck \leftarrow \mathsf {Setup}(1^\lambda )\) generates a commitment key ck, which specifies a message space \(\mathcal {M}_{ck}\), a randomness space \(\mathcal {R}_{ck}\) and a commitment space \(\mathcal {C}_{ck}\). The commitment algorithm \(\mathsf {Com}\) defines a function \(\mathsf {Com}_{ck} : \mathcal {M}_{ck} \times \mathcal {R}_{ck} \rightarrow \mathcal {C}_{ck}\). On input of \(m \in \mathcal {M}_{ck}\), the sender randomly chooses  and computes a commitment string \(c = \mathsf {Com}_{ck}(m, r) \in \mathcal {C}_{ck}\).
and computes a commitment string \(c = \mathsf {Com}_{ck}(m, r) \in \mathcal {C}_{ck}\).
A commitment is perfectly hiding if, for any \(m \in \mathcal {M}_{ck} \), the distribution  is statistically independent of m. It is perfectly binding if any element of the commitment space \(\mathcal {C}_{ck}\) uniquely determines the message. Groth and Kohlweiss [24] use the following additional properties.
is statistically independent of m. It is perfectly binding if any element of the commitment space \(\mathcal {C}_{ck}\) uniquely determines the message. Groth and Kohlweiss [24] use the following additional properties.
Definition 6
A commitment scheme \((\mathsf {Setup}, \mathsf {Com})\) is strongly binding if, for any PPT adversary \(\mathcal {A}\), there exists a negligible function \(\varepsilon (\lambda )\) such that
We consider a prime \(q > 2^\lambda \) specified in the commitment key ck. The message space and the randomness space are both \(\mathcal {M}_{ck}=\mathcal {R}_{ck}=\mathbb {Z}_q\).
Definition 7
A commitment scheme \((\mathsf {Setup}, \mathsf {Com})\) is additively homomorphic if for all messages \(m_1, m_2 \in \mathcal {M}_{ck}\) and all random coins \(r_1, r_2 \in \mathcal {R}_{ck}\), we have \(\mathsf {Com}_{ck}( m_1; r_1) \cdot \mathsf {Com}_{ck}( m_2; r_2) = \mathsf {Com}_{ck} (m_1 + m_2; r_1 + r_2).\)
B Deferred Proofs for the Fully Tight Construction
1.1 B.1 Proof of Lemma 3
Proof
The only situation where Game 5 differs from Game 4 is the event \(F_5\) that extracting \(\{ \varvec{C}_{\ell _j}^\star \}_{j=1}^n\) leads to a string \(\ell ^\star \in \{0,1\}^n\) but \((T_0^\star ,T_1^\star )\) does not decrypt to an encoding \(U^{\alpha _{\ell ^\star }} \cdot V^{\beta _{\ell ^\star }}\) of the \(\ell ^\star \)-th ring member’s secret key. This implies that \(\varvec{V}_{\ell ^\star } =(X_{\ell ^\star },Y_{\ell ^\star },T_0^\star ,T_1^\star )\) is not in the column space of \(\mathbf {M}_H\) (as defined in (3)) and we show that this event can only happen with probability \(Q_{\mathcal {H}_\mathsf {FS}} \cdot n /q \le Q_{\mathcal {H}_\mathsf {FS}} \cdot \log (Q_V)/q\), where \(n =\log N^\star \).
Note that (10) implies that \(f_j^\star \) equals \(f_j^\star =a_j^\star + \ell _j^\star \cdot x^\star \) for all \(j \in [n]\), where \(a_j^\star \in \mathbb {Z}_q\) is encrypted by \(\varvec{C}_{a_j}^\star \). Defining \(f_{j,1}^\star = f_j^\star \) and \(f_{j,0}^\star =x -f_j^\star \), we know that
for some \(p_{i,0}^\star ,\ldots ,p_{i,n-1}^\star \in \mathbb {Z}_q\). This implies
Moreover, the last verification Eq. (11) implies
By taking the discrete logarithms \(\log _g( \cdot )\) of both members of (15), we get
Since \(\mathbf {L}_h\) has rank at most 3 due to the modification introduced in Game 2 and Game 3, assuming that \(\varvec{v}_{\ell ^\star }=\log _g(\varvec{V}_{\ell ^\star }) \in \mathbb {Z}_q^4\) is not in the column space of \(\mathbf {L}_h\), there exists a non-zero vector \(\varvec{t} \in \mathbb {Z}_q^4\) such that \( \varvec{t}^\top \cdot \mathbf {L}_h = \mathbf {0}^{1 \times 4}\) and \(\varvec{t}^\top \cdot \varvec{v}_{\ell ^\star } \ne 0\). If we multiply both members of (16) on the left by \( \varvec{t}^\top \), we obtain
If \(\varvec{t}^\top \cdot \varvec{v}_{\ell ^\star } \ne 0\), equality (17) implies that x is a root of a non-zero polynomial of degree n. However, x is uniformly distributed over \(\mathbb {Z}_q\) and the Schwartz-Zippel Lemma implies that (17) can only hold with probability \(n/q < \log (Q_V)/q\).
In order to bound the probability \(\Pr [F_5]\), we have to consider all hash queries \(H_{FS}(M, \mathcal {R}, T_0, T_1, \{ \varvec{C}_{\ell _j} , \varvec{C}_{a_j}, \varvec{C}_{b_j}, \varvec{C}_{d_{j-1}}\}_{j=1}^n)\) for which \(\mathcal {R}\) only contains honestly generated keys and \((T_0,T_1)\) does not decrypt to an encoding \(U^{\alpha _\ell } \cdot V^{\beta _\ell }\) of the \(\ell \)-th key of \(\mathcal {R}\), where \(\ell \in \{0,\ldots ,|\mathcal {R}|-1\}\) is determined by \(\{ \varvec{C}_{\ell _j}\}_{j=1}^n\). Taking a union bound over all hash queries, we obtain \( \Pr [F_5] \le Q_{\mathcal {H}_\mathsf {FS}} \cdot \log (Q_V)/q\). \(\square \)
Rights and permissions
Copyright information
© 2018 Springer Nature Switzerland AG
About this paper
Cite this paper
Libert, B., Peters, T., Qian, C. (2018). Logarithmic-Size Ring Signatures with Tight Security from the DDH Assumption. In: Lopez, J., Zhou, J., Soriano, M. (eds) Computer Security. ESORICS 2018. Lecture Notes in Computer Science(), vol 11099. Springer, Cham. https://doi.org/10.1007/978-3-319-98989-1_15
Download citation
DOI: https://doi.org/10.1007/978-3-319-98989-1_15
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-98988-4
Online ISBN: 978-3-319-98989-1
eBook Packages: Computer ScienceComputer Science (R0)