
Fuchsia is an open-source capability-based operating system developed by Google. In contrast to Google's Linux-based operating systems such as ChromeOS and Android, Fuchsia is based on a custom kernel named Zircon. It publicly debuted as a self-hosted git repository in August 2016 without any official corporate announcement. After years of development, its official product launch was in 2021 on th

On a very high level, the main elements in valuing a corporate by Discounted Cash Flow are as follows; see Valuation using discounted cash flows, and graphics below, for detail: Free Cash Flow Projections: Projections of the amount of Cash produced by a company's business operations after paying for operating expenses and capital expenditures.[1] Discount Rate: The cost of capital (Debt and Equity

In materials management, ABC analysis is an inventory categorisation technique which divides inventory into three categories: 'A' items, with very tight control and accurate records, 'B' items, less tightly controlled and with moderate records, and 'C' items, with the simplest controls possible and minimal records. An ABC analysis provides a mechanism for identifying items that will have a signifi

Ethnography is a branch of anthropology and the systematic study of individual cultures. Ethnography explores cultural phenomena from the point of view of the subject of the study. Ethnography is also a type of social research that involves examining the behavior of the participants in a given social situation and understanding the group members' own interpretation of such behavior.[1] As a form o

In marketing, market segmentation or customer segmentation is the process of dividing a consumer or business market into meaningful sub-groups of current or potential customers (or consumers) known as segments.[1] Its purpose is to identify profitable and growing segments that a company can target with distinct marketing strategies. In dividing or segmenting markets, researchers typically look for
A core competency is a concept in management theory introduced by C. K. Prahalad and Gary Hamel.[1] It can be defined as "a harmonized combination of multiple resources and skills that distinguish a firm in the marketplace" and therefore are the foundation of companies' competitiveness.[2] Core competencies fulfill three criteria:[1] Provides potential access to a wide variety of markets. Should m

This article needs additional citations for verification. Please help improve this article by adding citations to reliable sources. Unsourced material may be challenged and removed. Find sources: "PEST analysis" – news · newspapers · books · scholar · JSTOR (September 2024) (Learn how and when to remove this message) In business analysis, PEST analysis (political, economic, social and technologica
In software engineering, service-oriented architecture (SOA) is an architectural style that focuses on discrete services instead of a monolithic design.[1] SOA is a good choice for system integration.[2] By consequence, it is also applied in the field of software design where services are provided to the other components by application components, through a communication protocol over a network. A
Business Process Outsourcing (BPO) is a subset of outsourcing that involves the contracting of the operations and responsibilities of a specific business process to a second-party service provider. Originally, this was associated with manufacturing firms, such as Coca-Cola that outsourced large segments of its supply chain.[1] BPO is typically categorized into back office outsourcing, which includ

Business process management (BPM) is the discipline in which people use various methods to discover, model, analyze, measure, improve, optimize, and automate business processes.[1][2] Any combination of methods used to manage a company's business processes is BPM.[3] Processes can be structured and repeatable or unstructured and variable. Though not required, enabling technologies are often used w
The WannaCry ransomware attack was a worldwide cyberattack in May 2017 by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency.[4] It was propagated using EternalBlue, an exploit developed by the United States National Security Agency (NSA) for Windows systems. Eter

A Universally Unique Identifier (UUID) is a 128-bit label used to uniquely identify objects in computer systems. The term Globally Unique Identifier (GUID) is also used, mostly in Microsoft systems.[1][2] When generated according to the standard methods, UUIDs are, for practical purposes, unique. Their uniqueness does not depend on a central registration authority or coordination between the parti

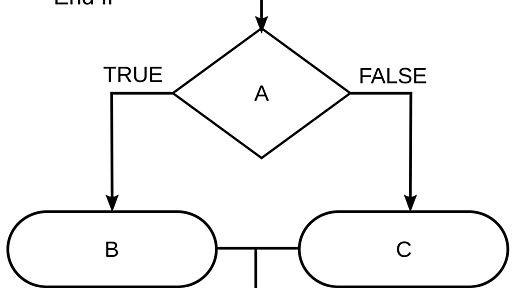
If-then-else flow diagram A nested if–then–else flow diagram In computer science, conditionals (that is, conditional statements, conditional expressions and conditional constructs) are programming language constructs that perform different computations or actions or return different values depending on the value of a Boolean expression, called a condition. Conditionals are typically implemented by
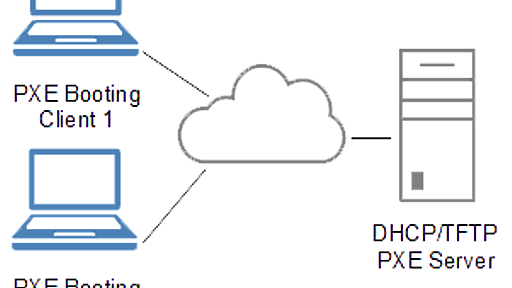
For an episode of the animated series Adventure Time, see Preboot. This article needs additional citations for verification. Please help improve this article by adding citations to reliable sources. Unsourced material may be challenged and removed. Find sources: "Preboot Execution Environment" – news · newspapers · books · scholar · JSTOR (May 2021) (Learn how and when to remove this message) A hi
Terraform is an infrastructure-as-code software tool created by HashiCorp. Users define and provide data center infrastructure using a declarative configuration language known as HashiCorp Configuration Language (HCL), or optionally JSON.[3] Terraform manages external resources (such as public cloud infrastructure, private cloud infrastructure, network appliances, software as a service, and platfo
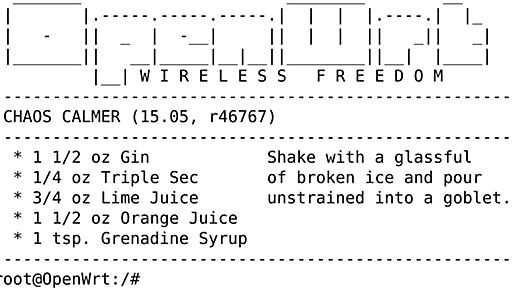
OpenWrt (from open wireless router) is an open-source project for embedded operating systems based on Linux, primarily used on embedded devices to route network traffic. The main components are Linux, util-linux, musl,[5] and BusyBox. All components have been optimized to be small enough to fit into the limited storage and memory available in home routers. OpenWrt is configured using a command-lin
リリース、障害情報などのサービスのお知らせ
最新の人気エントリーの配信
処理を実行中です
j次のブックマーク
k前のブックマーク
lあとで読む
eコメント一覧を開く
oページを開く