OSI Model From Layer 1 to Layer 3
OSI Model From Layer 1 to Layer 3
Uploaded by
lynnunderwaterCopyright:
Available Formats
OSI Model From Layer 1 to Layer 3
OSI Model From Layer 1 to Layer 3
Uploaded by
lynnunderwaterCopyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Copyright:
Available Formats
OSI Model From Layer 1 to Layer 3
OSI Model From Layer 1 to Layer 3
Uploaded by
lynnunderwaterCopyright:
Available Formats
Day Two – OSI Model from Layer 1 to Layer 3 Doc.
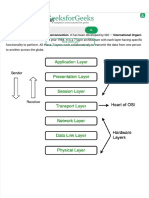
OSI Model
The OSI Model Defined
The OSI Model (Open Systems Interconnection Model) is a conceptual framework used to describe the
functions of a networking system. The OSI model characterizes computing functions into a universal set
of rules and requirements in order to support interoperability between different products and software.
In the OSI reference model, the communications between a computing system are split into seven
different abstraction layers: Physical, Data Link, Network, Transport, Session, Presentation, and
Application.
Created at a time when network computing was in its infancy, the OSI was published in 1984 by the
International Organization for Standardization (ISO). Though it does not always map directly to specific
systems, the OSI Model is still used today as a means to describe Network Architecture.
The OSI has been design to work over a 7-layer model flow. Each layer interact with each other to
provide final results as expected.
Please find a reference of the 7 different layers that compose the OSI model on the following chart:
Juniper Business Use Only
Physical Layer
The physical layer is literally the physical hardware that makes up the network. This layer has several major
functions:
•Defining physical specifications
•Defining protocols
•Defining transmission mode (half duplex & full duplex)
•Defining the network’s topology
•Represents the electrical and physical portion of the system.
*Transmission and reception of raw of bit streams over a physical medium*
Functions of Physical Layer
Following are the various functions performed by the Physical layer of the OSI model.
Juniper Business Use Only
1. Representation of Bits: Data in this layer consists of stream of bits. The bits must be encoded
into signals for transmission. It defines the type of encoding i.e. how 0's and 1's are changed to
signal.
2. Data Rate: This layer defines the rate of transmission which is the number of bits per second.
3. Synchronization: It deals with the synchronization of the transmitter and receiver. The sender
and receiver are synchronized at bit level.
4. Interface: The physical layer defines the transmission interface between devices and
transmission medium.
5. Line Configuration: This layer connects devices with the medium: Point to Point configuration
and Multipoint configuration.
6. Topologies: Devices must be connected using the following topologies: Mesh, Star, Ring and Bus.
7. Transmission Modes: Physical Layer defines the direction of transmission between two devices:
Simplex, Half Duplex, Full Duplex.
8. Deals with baseband and broadband transmission.
Juniper Business Use Only
Data Link Layer
•The Data Link Layer provides node-to-node data transfer (between two directly connected nodes), and also
handles error correction from the physical layer.
•Two sublayers exist here as well - the Media Access Control (MAC) layer and the Logical Link Control (LLC)
layer.
•In the networking world, most switches operate at Layer 2 .
*Reliable transmission of data frames between two nodes connected by a physical layer*
Logical link control sublayer
The uppermost sublayer, LLC, multiplexes protocols running at the top of data link layer, and optionally
provides flow control, acknowledgment, and error notification. The LLC provides addressing and control
of the data link. It specifies which mechanisms are to be used for addressing stations over the
transmission medium and for controlling the data exchanged between the originator and recipient
machines.
Media access control sublayer
MAC may refer to the sublayer that determines who is allowed to access the media at any one time
(e.g. CSMA/CD). Other times it refers to a frame structure delivered based on MAC addresses inside.
There are generally two forms of media access control: distributed and centralized. Both of these may
be compared to communication between people. In a network made up of people speaking, i.e. a
conversation, they will each pause a random amount of time and then attempt to speak again,
effectively establishing a long and elaborate game of saying "no, you first".
Accessing the media
As with each of the OSI layers, there are terms specific to this layer:
Frame - The Data Link layer PDU
Node - The Layer 2 notation for network devices connected to a common medium
Media/medium (physical)* - The physical means for the transfer of information between two nodes
Network (physical)** - Two or more nodes connected to a common medium
Juniper Business Use Only
The Data Link layer is responsible for the exchange of frames between nodes over the media of a
physical network.
* It is important to understand the meaning of the words medium and media within the context of this
chapter. Here, these words refer to the material that actually carries the signals representing the
transmitted data. Media is the physical copper cable, optical fiber, or atmosphere through which the
signals travel. In this chapter media does not refer to content programming such as audio, animation,
television, and video as used when referring to digital content and multimedia.
** A physical network is different from a logical network. Logical networks are defined at the Network
layer by the arrangement of the hierarchical addressing scheme. Physical networks represent the
interconnection of devices on a common media. Sometimes, a physical network is also referred to as a
network segment.
Creating a frame
The Data Link layer prepares a packet for transport across the local media by encapsulating it with a
header and a trailer to create a frame. Unlike the other PDUs that have been discussed in this course,
the Data Link layer frame includes:
Data - The packet from the Network layer
Header - Contains control information, such as addressing, and is located at the beginning of the
PDU
Trailer - Contains control information added to the end of the PDU
Full Duplex and Half Duplex (see image)
Layer 2 header
The frame header contains the control information specified by the Data Link layer protocol for the
specific logical topology and media used. Frame control information is unique to each type of protocol.
It is used by the Layer 2 protocol to provide features demanded by the communication environment.
Typical frame header fields include:
Start Frame field - Indicates the beginning of the frame
Source and Destination address fields - Indicates the source and destination nodes on the media
Priority/Quality of Service field - Indicates a particular type of communication service for
processing
Type field - Indicates the upper layer service contained in the frame
Logical connection control field - Used to establish a logical connection between nodes
Physical link control field - Used to establish the media link
Flow control field - Used to start and stop traffic over the media
Congestion control field - Indicates congestion in the media
Juniper Business Use Only
Network layer
The Network layer, or OSI Layer 3, provides services to exchange the individual pieces of data over the
network between identified end devices.
*Structuring and managing multimode network, including addressing, routing and traffic control*
To accomplish this end-to-end transport, Layer 3 uses four basic processes:
Addressing: the Network layer must provide a mechanism for addressing these end devices. If
individual pieces of data are to be directed to an end device, that device must have a unique
address. In an IPv4 network, when this address is added to a device, the device is then referred
to as a host.
Encapsulation: the Network layer must provide encapsulation. Not only must the devices be
identified with an address, the individual pieces - the Network layer PDUs - must also contain
these addresses. During the encapsulation process, Layer 3 receives the Layer 4 PDU and adds a
Layer 3 header, or label, to create the Layer 3 PDU. When referring to the Network layer, we call
this PDU a packet. When a packet is created, the header must contain, among other information,
the address of the host to which it is being sent. This address is referred to as the destination
address. The Layer 3 header also contains the address of the originating host. This address is
called the source address. After the Network layer completes its encapsulation process, the
packet is sent down to the Data Link layer to be prepared for transportation over the media.
Routing: the Network layer must provide services to direct these packets to their destination
host. The source and destination hosts are not always connected to the same network. In fact,
the packet might have to travel through many different networks. Along the way, each packet
must be guided through the network to reach its final destination. Intermediary devices that
connect the networks are called routers. The role of the router is to select paths for and direct
packets toward their destination. This process is known as routing. During the routing through
an internetwork, the packet may traverse many intermediary devices. Each route that a packet
takes to reach the next device is called a hop. As the packet is forwarded, its contents (the
Transport layer PDU), remain intact until the destination host is reached.
Decapsulation: the packet arrives at the destination host and is processed at Layer 3. The host
examines the destination address to verify that the packet was addressed to this device. If the
address is correct, the packet is decapsulated by the Network layer and the Layer 4 PDU
contained in the packet is passed up to the appropriate service at Transport layer. Unlike the
Transport layer (OSI Layer 4), which manages the data transport between the processes running
on each end host, Network layer protocols specify the packet structure and processing used to
carry the data from one host to another host. Operating without regard to the application data
carried in each packet allows the Network layer to carry packets for multiple types of
communications between multiple hosts.
Routing protocols vs. Routed protocols
Routing protocols are the means by which routers exchange next hop reachability through destinations
while routed protocols are the traffic that routers direct from source to destination using the routing
protocols.
Juniper Business Use Only
Routing protocols Routed protocols
OSPF IP
BGP IPX
IS-IS Apple talk
RIP SSH
SIP
IP
IP has the task of delivering packets from the source host to the destination host solely based on the IP
addresses in the packet headers. For this purpose, IP defines packet structures that encapsulate the data
to be delivered. It also defines addressing methods that are used to label the datagram with source and
destination information.
IPv4
IPv4 is a connectionless protocol, and operates on a best effort delivery model, in that it does not
guarantee delivery, nor does it assure proper sequencing or avoidance of duplicate delivery. These
aspects, including data integrity, are addressed by an upper layer transport protocol, such as the
Transmission Control Protocol (TCP).
IPv4 uses 32-bit addresses which limits the address space to 4294967296 (232) addresses.
IPv6
IPv6 provides other technical benefits in addition to a larger addressing space. In particular, it permits
hierarchical address allocation methods that facilitate route aggregation across the Internet, and thus
limit the expansion of routing tables. The use of multicast addressing is expanded and simplified, and
provides additional optimization for the delivery of services. Device mobility, security, and configuration
aspects have been considered in the design of the protocol.
IPv6 addresses are represented as eight groups, separated by colons, of four hexadecimal digits.
IP v4 Packet Header
An IPv4 protocol defines many different fields in the packet header. These fields contain binary values
that the IPv4 services reference as they forward packets across the network.
Fields:
IP Source Address
IP Destination Address
Time-to-Live (TTL)
Type-of-Service (ToS)
Juniper Business Use Only
Protocol
Fragment Offset
IP Destination Address
The IP Destination Address field contains a 32-bit binary value that represents the packet destination
Network layer host address.
IP Source Address
The IP Source Address field contains a 32-bit binary value that represents the packet source Network
layer host address.
Time-to-Live
The Time-to-Live (TTL) is an 8-bit binary value that indicates the remaining "life" of the packet. The TTL
value is decreased by at least one each time the packet is processed by a router (that is, each hop).
When the value becomes zero, the router discards or drops the packet and it is removed from the
network data flow. This mechanism prevents packets that cannot reach their destination from being
forwarded indefinitely between routers in a routing loop. If routing loops were permitted to continue,
the network would become congested with data packets that will never reach their destination.
Decrementing the TTL value at each hop ensures that it eventually becomes zero and that the packet
with the expired TTL field will be dropped.
Protocol
This 8-bit binary value indicates the data payload type that the packet is carrying. The Protocol field
enables the Network layer to pass the data to the appropriate upper-layer protocol.
Example values are:
01 ICMP
06 TCP
17 UDP
Type-of-Service
The Type-of-Service field contains an 8-bit binary value that is used to determine the priority of each
packet. This value enables a Quality-of-Service (QoS) mechanism to be applied to high priority packets,
such as those carrying telephony voice data. The router processing the packets can be configured to
decide which packet it is to forward first based on the Type-of-Service value.
Fragment Offset
A router may have to fragment a packet when forwarding it from one medium to another medium that
has a smaller MTU. When fragmentation occurs, the IPv4 packet uses the Fragment Offset field and the
Juniper Business Use Only
MF flag in the IP header to reconstruct the packet when it arrives at the destination host. The fragment
offset field identifies the order in which to place the packet fragment in the reconstruction.
More Fragments flag
The More Fragments (MF) flag is a single bit in the Flag field used with the Fragment Offset for the
fragmentation and reconstruction of packets. The More Fragments flag bit is set, it means that it is not
the last fragment of a packet. When a receiving host sees a packet arrive with the MF = 1, it examines
the Fragment Offset to see where this fragment is to be placed in the reconstructed packet. When a
receiving host receives a frame with the MF = 0 and a non-zero value in the Fragment offset, it places
that fragment as the last part of the reconstructed packet. An unfragmented packet has all zero
fragmentation information (MF = 0, fragment offset =0).
Don't Fragment flag
The Don't Fragment (DF) flag is a single bit in the Flag field that indicates that fragmentation of the
packet is not allowed. If the Don't Fragment flag bit is set, then fragmentation of this packet is NOT
permitted. If a router needs to fragment a packet to allow it to be passed downward to the Data Link
layer but the DF bit is set to 1, then the router will discard this packet.
Other fields:
Version - Contains the IP version number (4).
Header Length (IHL) - Specifies the size of the packet header.
Packet Length - This field gives the entire packet size, including header and data, in bytes.
Identification - This field is primarily used for uniquely identifying fragments of an original IP packet.
Header Checksum - The checksum field is used for error checking the packet header.
Options - There is provision for additional fields in the IPv4 header to provide other services, but these
are rarely used.
IP classes
Class A: The first bit of the first octet is always set to 0 (zero). Thus the first octet ranges from 1
– 127. Class A addresses only include IP starting from 1.x.x.x to 126.x.x.x only. The IP range
127.x.x.x is reserved for loopback IP addresses.
The default subnet mask for Class A IP address is 255.0.0.0 which implies that Class A addressing
can have 126 networks (27-2) and 16777214 hosts (224-2).
Class B: An IP address which belongs to class B has the first two bits in the first octet set to 10.
Juniper Business Use Only
The IP Addresses range from 128.0.x.x to 191.255.x.x. The default subnet mask for Class B is
255.255.x.x. Class B has 16384 (214) Network addresses and 65534 (216-2) Host addresses.
Class C: The first octet of Class C IP address has its first 3 bits set to 110. The addresses range
from 192.0.0.x to 223.255.255.x. The default subnet mask for Class C is 255.255.255.x. Class C
gives 2097152 (221) Network addresses and 254 (28-2) Host addresses.
Juniper Business Use Only
You might also like
- Chapter7 Data Link LayerDocument91 pagesChapter7 Data Link LayerGladys EliverNo ratings yet
- NetworkDocument21 pagesNetworktabassi199100% (1)
- CCNA 1 Chapter 7 NotesDocument7 pagesCCNA 1 Chapter 7 Notesdercole69No ratings yet
- 7 Data Link LayerDocument35 pages7 Data Link LayerRashed ZamanNo ratings yet
- Data Link LayerDocument9 pagesData Link LayerAndres GonzalezNo ratings yet
- CCNA Exploration - Network Fundamentals 7 Data Link Layer 7.0 Chapter Introduction 7.0.1 Chapter IntroductionDocument35 pagesCCNA Exploration - Network Fundamentals 7 Data Link Layer 7.0 Chapter Introduction 7.0.1 Chapter IntroductiongetagetagetaNo ratings yet
- Unit 1 BDocument79 pagesUnit 1 BVeena Divya KrishnappaNo ratings yet
- CISCO-7 Data Link LayerDocument27 pagesCISCO-7 Data Link LayerPraveen KumarNo ratings yet
- Osi & TCP NotesDocument15 pagesOsi & TCP NotesAnuradha JadiyaNo ratings yet
- 7 Data Link LayerDocument46 pages7 Data Link LayerniiloyNo ratings yet
- Computer Network ModelDocument14 pagesComputer Network ModelDan TamiruNo ratings yet
- Network and System UNIT 2 NotesDocument24 pagesNetwork and System UNIT 2 Notespinkyjaiswal7890No ratings yet
- CN ppt1 OSIDocument34 pagesCN ppt1 OSIprathamdhobi360No ratings yet
- UNIT 1 Computer Networks NotesDocument18 pagesUNIT 1 Computer Networks NotesdoctoraseenNo ratings yet
- CS -II Unit V (1)Document46 pagesCS -II Unit V (1)pramidibalu2005No ratings yet
- Networking Lecture Summary 2Document7 pagesNetworking Lecture Summary 2Reaper XNo ratings yet
- CN Notes by MohanDocument17 pagesCN Notes by MohanMohan Raj KNo ratings yet
- Layers of OSI Model - GeeksforGeeksDocument9 pagesLayers of OSI Model - GeeksforGeeksHelp DeskNo ratings yet
- 3.1 OSI ModelDocument6 pages3.1 OSI ModelSuyasha JainNo ratings yet
- Internetworking Models: Model Was Created by The International Organization ForDocument45 pagesInternetworking Models: Model Was Created by The International Organization Forkerya ibrahimNo ratings yet
- CN QB Solutions 111Document68 pagesCN QB Solutions 111Devanshi DaveNo ratings yet
- Layers of OSI Model PDFDocument9 pagesLayers of OSI Model PDFppskyNo ratings yet
- Osi ModelDocument2 pagesOsi ModelHalcyon LizardoNo ratings yet
- Unit 2 The Reference ModelDocument14 pagesUnit 2 The Reference Modelpatelcd1234567890No ratings yet
- CIT 118 Lecture 2 (A) Protocols and ArchitectureDocument6 pagesCIT 118 Lecture 2 (A) Protocols and ArchitectureJames GitongaNo ratings yet
- Unit 2 BBA VDocument32 pagesUnit 2 BBA Vaakanshatyagi030303No ratings yet
- TCP IP NotesDocument107 pagesTCP IP Notes9033373180No ratings yet
- TCP Ip NotesDocument105 pagesTCP Ip Notesprasadpra17No ratings yet
- Basics of Computer NetworkingDocument8 pagesBasics of Computer Networkingwesen destaNo ratings yet
- Advance Computer NetworkDocument15 pagesAdvance Computer NetworkIffat KhanNo ratings yet
- Distributed e SysDocument7 pagesDistributed e SysHemaNo ratings yet
- OSI Model 7 Layers Explained in Computer NetworkDocument8 pagesOSI Model 7 Layers Explained in Computer NetworkjhhjnNo ratings yet
- OSI ModelDocument7 pagesOSI ModelK KiranmayiNo ratings yet
- Computer NetworkDocument3 pagesComputer NetworkMubashir SheikhNo ratings yet
- What Is OSI Model 17.01.2024Document7 pagesWhat Is OSI Model 17.01.2024aloishp36No ratings yet
- Micro CNDocument24 pagesMicro CNjunaidcheeta59No ratings yet
- Layers of Osi ModelDocument18 pagesLayers of Osi ModelArthi AnnamallaNo ratings yet
- Networking_BasicsDocument13 pagesNetworking_BasicsRakshit pareekNo ratings yet
- What is OSI ModelDocument13 pagesWhat is OSI ModelRakshit pareekNo ratings yet
- OSI ModelDocument11 pagesOSI ModelAdi AcharyaNo ratings yet
- OSI Model - pdf3Document13 pagesOSI Model - pdf3itachigood980No ratings yet
- DC and CN Chapt-5-1Document88 pagesDC and CN Chapt-5-1habtamud655No ratings yet
- What Is OSI ModelDocument18 pagesWhat Is OSI Modelsoulxd1910No ratings yet
- ECE541 Data Network 1: Communicating Over The NetworkDocument37 pagesECE541 Data Network 1: Communicating Over The NetworkAzri AzsrNo ratings yet
- IOT - UNIT IVDocument94 pagesIOT - UNIT IVimranNo ratings yet
- Compare and Contrast OSI and TCP-IP ModelsDocument28 pagesCompare and Contrast OSI and TCP-IP Modelsjemsson66No ratings yet
- Layers of OSI ModelDocument5 pagesLayers of OSI Modelcivike100% (1)
- Layers of OSI Model.Document6 pagesLayers of OSI Model.tahir ullahNo ratings yet
- On Tap CKDocument24 pagesOn Tap CKHoàng DươngNo ratings yet
- OSI Model PDFDocument9 pagesOSI Model PDFjonrey lumayagNo ratings yet
- Computer Networks-Module1Document34 pagesComputer Networks-Module1Sreedevi YashpalNo ratings yet
- CS6551Document103 pagesCS6551rishikarthick0% (1)
- Unit 04 OSI Reference Model - Part-1Document15 pagesUnit 04 OSI Reference Model - Part-1roysayanccp05No ratings yet
- Network TopologyDocument5 pagesNetwork Topologylalchhanhimahrahsel44No ratings yet
- IT Practical ProjectDocument16 pagesIT Practical Projectakanksha.lingwal2004No ratings yet
- Wpan & WlanDocument24 pagesWpan & WlanChristian ZetaNo ratings yet
- Osi ModelDocument6 pagesOsi ModelShujaNo ratings yet
- Lec 2Document13 pagesLec 2muhammadijaz.figmaNo ratings yet
- Osi Reference ModelDocument43 pagesOsi Reference ModelMashaka YohanaNo ratings yet
- Cisco Certified Network Associate (CCNA) and Cisco Certified Network Professional (CCNP): Mastering Network Automation and Programmability Study GuideFrom EverandCisco Certified Network Associate (CCNA) and Cisco Certified Network Professional (CCNP): Mastering Network Automation and Programmability Study GuideNo ratings yet
- S OP Mind Map 1568467991Document1 pageS OP Mind Map 1568467991MehmetNo ratings yet
- Milestone 2Document6 pagesMilestone 2RIYANo ratings yet
- Asternic Callcenter Stats Admin GuideDocument16 pagesAsternic Callcenter Stats Admin GuideFarrukh AhmedNo ratings yet
- Membuat Website Tanpa CodingDocument3 pagesMembuat Website Tanpa CodingAmanda Muchsin ChalikNo ratings yet
- Casp LabDocument7 pagesCasp LabGPT149 NBANo ratings yet
- STM8 Bootloader - STMicroelectronics - 240630 - 222004Document73 pagesSTM8 Bootloader - STMicroelectronics - 240630 - 222004willppNo ratings yet
- Acta TribologicaDocument146 pagesActa TribologicaCiotea Mariana100% (1)
- MSADocument18 pagesMSANdomaduNo ratings yet
- Solidcast ManualDocument67 pagesSolidcast ManualMIGUEL LEYVANo ratings yet
- PHP PPTDocument9 pagesPHP PPTdeepblue5991No ratings yet
- Supercomputer: ExamplesDocument6 pagesSupercomputer: ExamplesSalman KhanNo ratings yet
- BGP MPLS Questions SetDocument4 pagesBGP MPLS Questions SetvelramsenNo ratings yet
- Web Application With Python and SecurityDocument4 pagesWeb Application With Python and Securityamani sayariNo ratings yet
- Getting Started Guide NXDocument22 pagesGetting Started Guide NXtvuongphamNo ratings yet
- Agena Tecno ProposalDocument12 pagesAgena Tecno ProposalAnde MamoNo ratings yet
- Lightning Protection According To IEC 62305Document119 pagesLightning Protection According To IEC 62305miguelgg78100% (4)
- App Distribution With FirebaseDocument14 pagesApp Distribution With FirebaseAshan KaushalyaNo ratings yet
- Probability Generating FunctionsDocument3 pagesProbability Generating FunctionsxkarebearNo ratings yet
- 100G Client Interface Evolution: Guylain Barlow JDSU Network & Service EnablementDocument31 pages100G Client Interface Evolution: Guylain Barlow JDSU Network & Service Enablementsrotenstein3114No ratings yet
- Risk Analytics (IMT) - Chapter 13Document19 pagesRisk Analytics (IMT) - Chapter 13shiva kulshresthaNo ratings yet
- M2 - 55348A - Administering Microsoft Endpoint Configuration Manager - SkillpipeDocument23 pagesM2 - 55348A - Administering Microsoft Endpoint Configuration Manager - SkillpipeDepolo PoloNo ratings yet
- Datasheet PDFDocument21 pagesDatasheet PDFXarhs KalimanisNo ratings yet
- Final (COMP 348-Summer2009)Document7 pagesFinal (COMP 348-Summer2009)Polina SolnishkoNo ratings yet
- Seminar Report On: Mobile Train Radio CommunicationDocument14 pagesSeminar Report On: Mobile Train Radio CommunicationHimanshu MishraNo ratings yet
- Linear Systems: Prof Sung-Ho HurDocument30 pagesLinear Systems: Prof Sung-Ho HurYousef BilbeisiNo ratings yet
- Menghitung Luas Dan Volume Balok Java CodeDocument19 pagesMenghitung Luas Dan Volume Balok Java CodeAdityaNo ratings yet
- E-Admit Card: Computer Based Examination For Recruitment To Paramedi Cal & Nursing Cadre Posts in EsicDocument3 pagesE-Admit Card: Computer Based Examination For Recruitment To Paramedi Cal & Nursing Cadre Posts in EsicVikas Kumar VermaNo ratings yet
- LN3C63 LiemicDocument13 pagesLN3C63 Liemichichem_scribdNo ratings yet
- Canterbury Institute of Management (CIM)Document9 pagesCanterbury Institute of Management (CIM)Suman GautamNo ratings yet
- 6 Legendary Lost Treasures That Are Still Up For Grabs - CrackedDocument7 pages6 Legendary Lost Treasures That Are Still Up For Grabs - CrackedSamuel Enrique Cano Patoc0% (1)